1 Introduction/Executive Summary
This report is an overview of the market for Privileged Access Management (PAM) platforms and provides a compass to help buyers find the product that best meets their needs. KuppingerCole examines the market segment, vendor capabilities, relative market share, and innovative approaches to providing PAM solutions. These platforms fall under the KuppingerCole Privileged Access Management PAM classification and add improved security and value to business.
Such products will include those that offer basic PAM capabilities such as password vaulting and management, full-service platforms that offer most capabilities right through to some CIEM capabilities and vendors that offer a mix of various capabilities for specific applications. The Leadership Compass is designed to address the fullest picture of the PAM market by assessing as many vendors as possible in the space, including those vendors to watch.
1.1 Highlights
- The emergence of Cloud Infrastructure Entitlement Platforms (CIEM) is disrupting the traditional PAM market; some traditional vendors now offering CIEM type capabilities.
- Dynamic cloud access demands continue to grow as organizations struggle with unauthorized clouds and personal cloud creation by Lines of Business (LOB), end users and Developers.
- New market entrants continue to appear but with highly focused PAM apps rather than suites, usually 100% cloud native.
- A market divide is emerging between centralized, multi-capability PAM platforms and smaller PAM and CIEM apps purchased for small businesses or LOBs
- Vaults vs. passwordless continues to be a choice but no sign yet of a persistent decline of vaults and password capabilities
- Just in Time (JIT) and Zero Standing Privilege (ZSP) demands are beginning to impact the market with vendors either now offering those capabilities or have in their roadmap.
- The number of PAM and PAM capable vendors (including Vendors to Watch) has increased despite mergers and acquisitions among established vendors.
- More granular and revised scoring by KuppingerCole has resulted in a realignment of vendors to reflect new capability demands and the changing market
- PAM Leadership Compass 2023 has revised Spider Graph categories to reflect changing market demands
- The overall Leaders are (in alphabetical order): ARCON, BeyondTrust, CyberArk, Delinea, EmpowerID, One Identity, Saviynt, Senhasegura and WALLIX.
1.2 Market Segment
Many successful cyber-attacks involve the misuse of privileged accounts, and misuse is enabled by inadequate Privileged Access Management (PAM) software, policies, or processes. Some of the malicious activities that must be detected and controlled are abuse of shared privileged credentials, misuse of elevated privileges by unauthorized users, theft of privileged credentials by cyber-criminals, and abuse of privileges on third-party systems accessed via the cloud.
Privileged accounts have traditionally given to a small set of administrators who needed access to perform maintenance and upgrade tasks, mostly on networks on-premises or local area networks (LAN). In some cases, senior employees may have also been given elevated access rights for specific tasks. It’s fair to say that this is no longer the case. Privilege management use cases now extend across entire organizations, with users and machines requiring task-based access to data, services, and applications held on legacy systems and multi-cloud-based infrastructures. All the while, admins still need to perform traditional privileged tasks.
PAM has evolved into a stronger and wider risk management discipline as digitalization has increased the attack surface to include cloud, multiple endpoints, home working, and no secure perimeters. It brings significant benefits to almost every major digital business initiative, including securing applications and data in the cloud, privileged user behaviour analytics to detect anomalous privileged behaviour and supporting endpoint threat protection More recently, several PAM vendors have started to accommodate capabilities that support Cloud Infrastructure Entitlement Management (CIEM) for cloud-based resources, and critical cloud-based workflows such as DevOps and CI/CD projects.
While there is overlap here, the demand for traditional PAM capabilities (vaulting, credential management, analytics, admin access, Endpoint Privilege Management etc.) remains robust and vendor efforts to improve on those capabilities continues to drive competition.
Support for the demands of digital organizations offered by the PAM tools is becoming a competitive differentiator in the PAM market. An important part of the Kuppinger PAM Leadership Compass is to evaluate the extent to which PAM vendors support digital business initiatives.
Both new and traditional vendors have responded well to demands for more advanced PAM capabilities suitable for the modern computing era. Interest in Least Privilege and Zero Trust informed architectures and policies has also grown as organizations look to secure the multi-cloud environments. Buyers are increasingly aware that a well-configured and up-to-date PAM platform can be an integral part of any such architecture and that the traditional architecture of PAM must be extended to support cloud environments and SaaS applications and services.
Regular readers of the PAM Leadership Compass will see that there has been a realignment of scatter chart positioning with some vendors shifting left compared to previous reports. This is because of an extended questionnaire and more granular process designed to reflect new capability demands and the changing market for privileged access solutions, particularly for cloud.
1.3 Delivery Models
This Leadership Compass is focused on PAM products that are offered in on-premises deployable form as an appliance or virtual appliance, in the cloud or as-a-service (PAMaaS) by the vendor. Some vendors also offer a MSSP option for third party services providers.
1.4 Required Capabilities
The KuppingerCole PAM Leadership Compass analyses and rates PAM platforms that cover the following key capabilities:
Classic PAM Capabilities
Account management
- Application to Application Password Management (AAPM)
- Password/credential vaulting
- Shared Account Password Management (SAPM)
- Privileged Session Management (PSM)
- Controlled Privilege Escalation and Delegation Management (CPEDM).
- Endpoint Privilege Management (EPM)
Authentication
- Just in Time Provisioning (JIT
- Privilege Single Sign-On (SSO)
- Multi Factor Authentication
Session management and analytics
- Fine grained access control
- Privileged Account Discovery and Lifecycle Manager (PADLM)
- Privileged User Behaviour Analytics (PUBA)
- Privileged Remote Access
- Session Recording and Monitoring (SRM)
Extended PAM
Account management
- Application to Application Password Management (AAPM)
- Controlled Privilege Escalation and Delegation Management (CPEDM)
- Privileged Remote Access
- DevOps support
Authentication
- Just in Time Provisioning (JIT)
- Ephemeral credentials
- CIEM
Session management and analytics
- Privilege IT task-based automation
- Privileged Access Governance
The PAM Leadership Compass analyzes software platforms that manage privileged access for:
- User identities
- Service identities
- Admin identities
- Machine identities
- API Identities
The PAM Leadership Compass covers software platforms that:
- Control privilege of identities of all kinds by enforcing Least Privilege across multi-hybrid environments
- Provide Privileged Access Management to those identities that have access to specific high-value and critical services, applications, and data in dynamic multi-hybrid environments
- Provide Just in Time access to services, applications, and data in dynamic multi-hybrid environments in line with security policies and business demands
- Manage entitlements of privileged identities with access to resources at the most granular level, enabling compliance with access governance policies.
- Manage multiple entities and all modern identity types including machine and non-machine
2 Leadership
Selecting a vendor of a product or service must not only be based on the information provided in a KuppingerCole Leadership Compass. The Leadership Compass provides a comparison based on standardized criteria and can help identifying vendors that shall be further evaluated. However, a thorough selection includes a subsequent detailed analysis and a Proof of Concept of pilot phase, based on the specific criteria of the customer.
2.1 Overall Leadership
Based on our rating, we created the various Leadership ratings. The Overall Leadership rating provides a combined view of the ratings for:
- Product
- Innovation
- Market
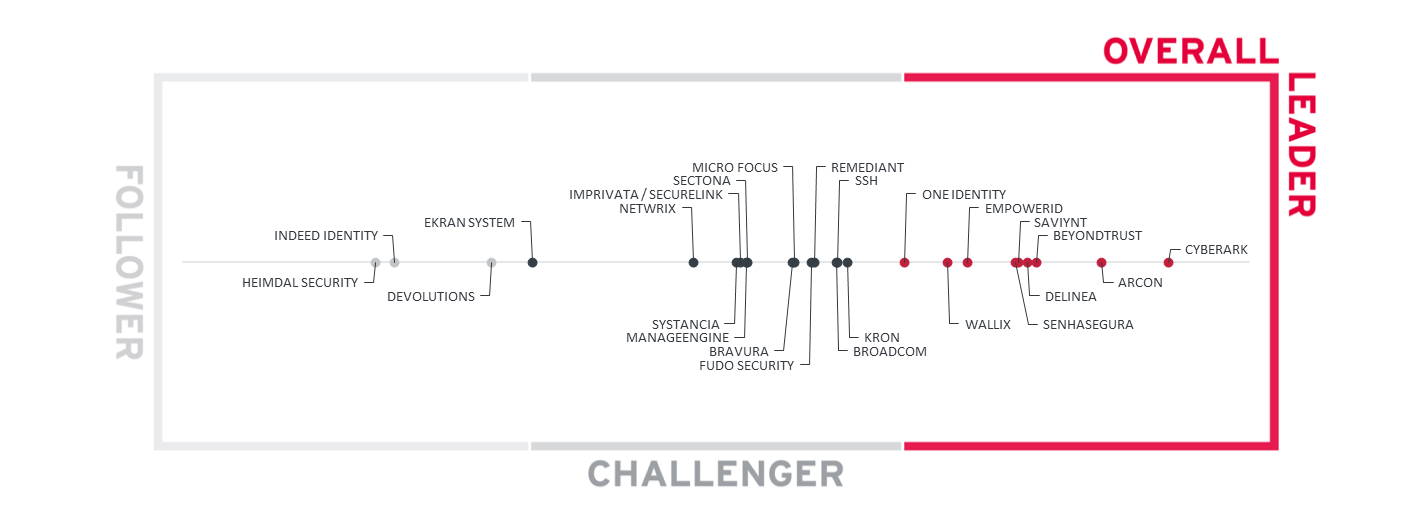
Figure 1: The overall leaders in PAM
The overall Leaders are (in alphabetical order):
- ARCON
- BeyondTrust
- CyberArk
- Delinea
- EmpowerID
- One Identity
- Saviynt
- Senhasegura
- WALLIX
2.2 Product Leadership
Product Leadership is the first specific category examined below. This view is mainly based on the analysis of service features and the overall capabilities of the various services.
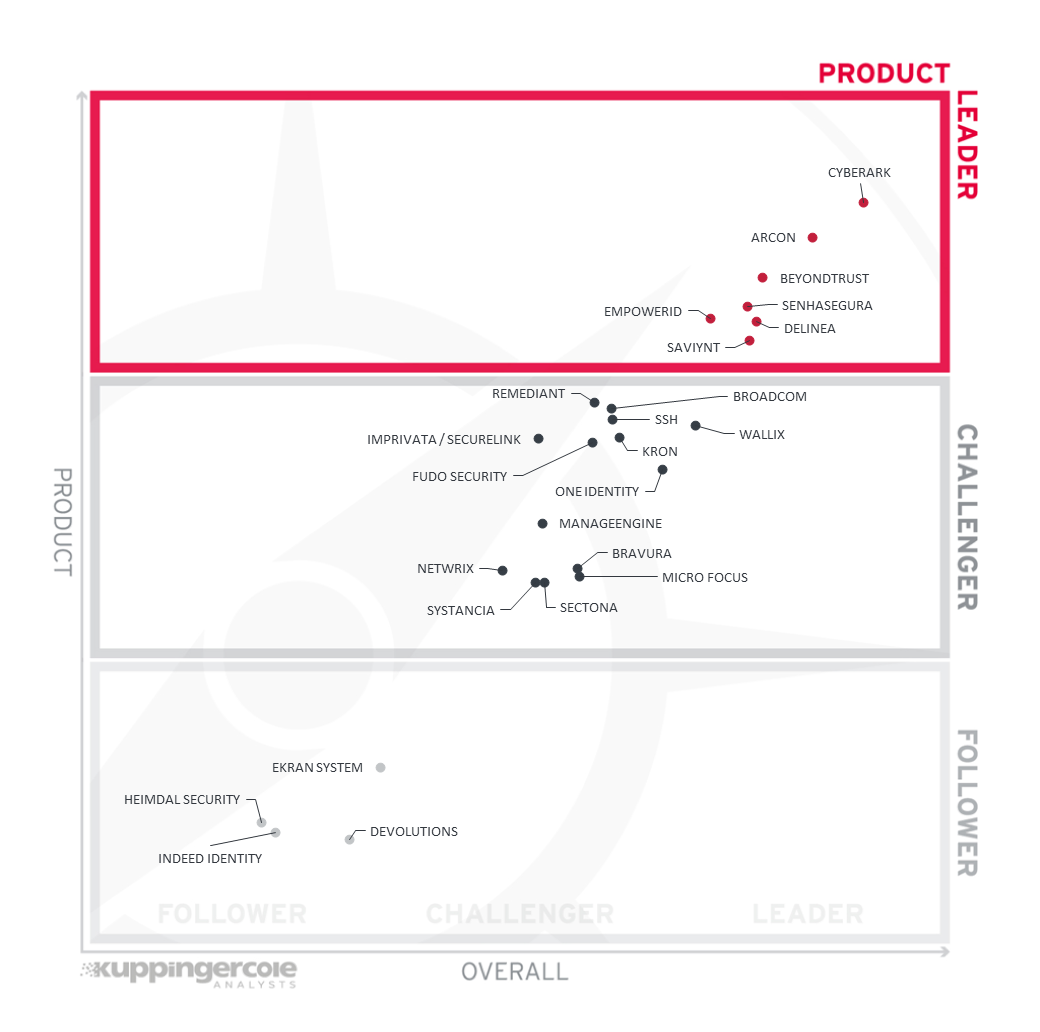
Figure 2: The product leaders PAM
The Product Leaders are (in alphabetical order):
- ARCON
- BeyondTrust
- CyberArk
- Delinea
- EmpowerID
- Senhasegura
- Saviynt
2.3 Innovation Leadership
Next, we examine innovation in the marketplace. Innovation is, from our perspective, a key capability in all IT market segments. Customers require innovation to meet evolving and even emerging business requirements. Innovation is not about delivering a constant flow of new releases. Rather, innovative companies take a customer-oriented upgrade approach, delivering customer-requested and other cutting-edge features, while maintaining compatibility with previous versions.
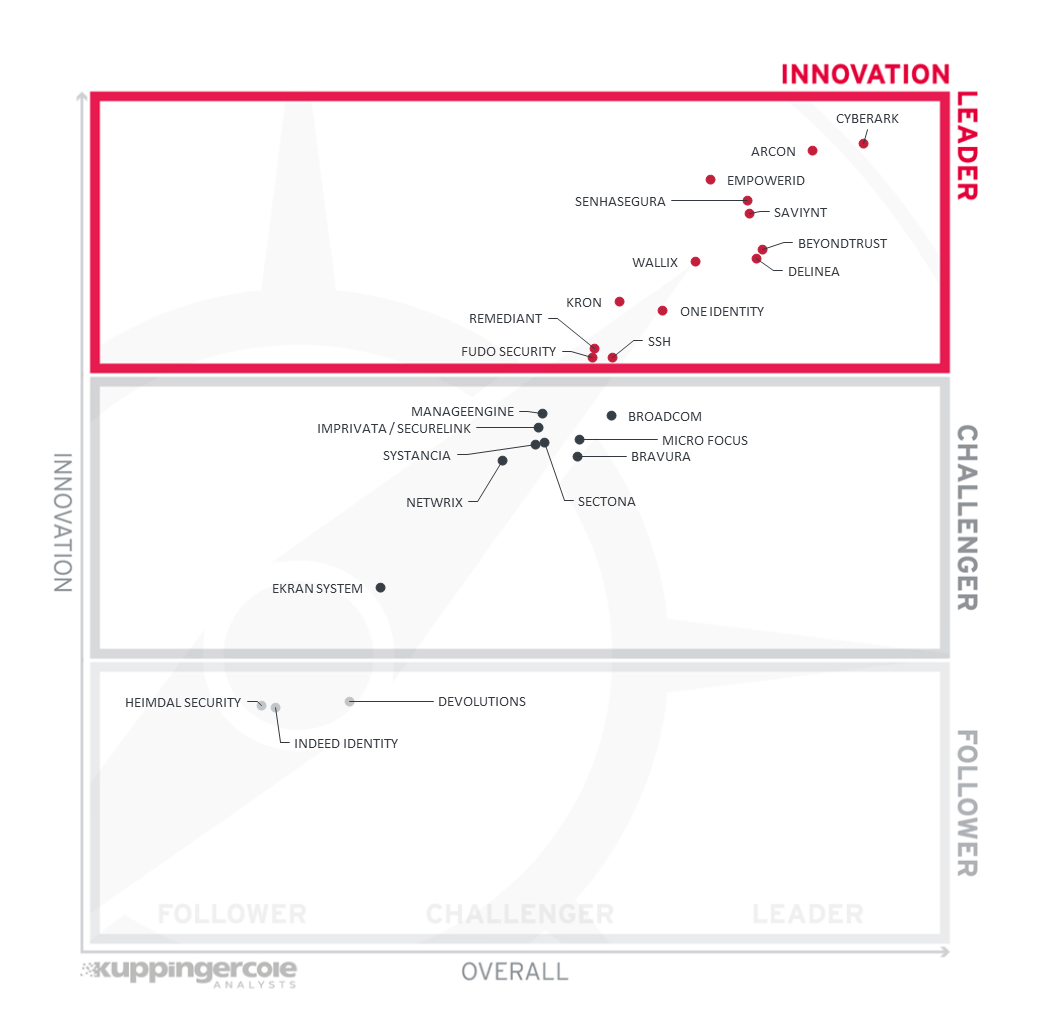
Figure 3: The innovation leaders in PAM
The Innovation Leaders are (in alphabetical order):
- ARCON
- BeyondTrust
- CyberArk
- Delinea
- EmpowerID
- Fudo Security
- Kron
- One Identity
- Remediant
- Saviynt
- Senhasegura
- SSH
- WALLIX
2.4 Market Leadership
Lastly, we analyze Market Leadership. This is an amalgamation of the number of customers, number of transactions evaluated, ratio between customers and managed identities/devices, the geographic distribution of customers, the size of deployments and services, the size and geographic distribution of the partner ecosystem, and financial health of the participating companies. Market Leadership, from our point of view, requires global reach.
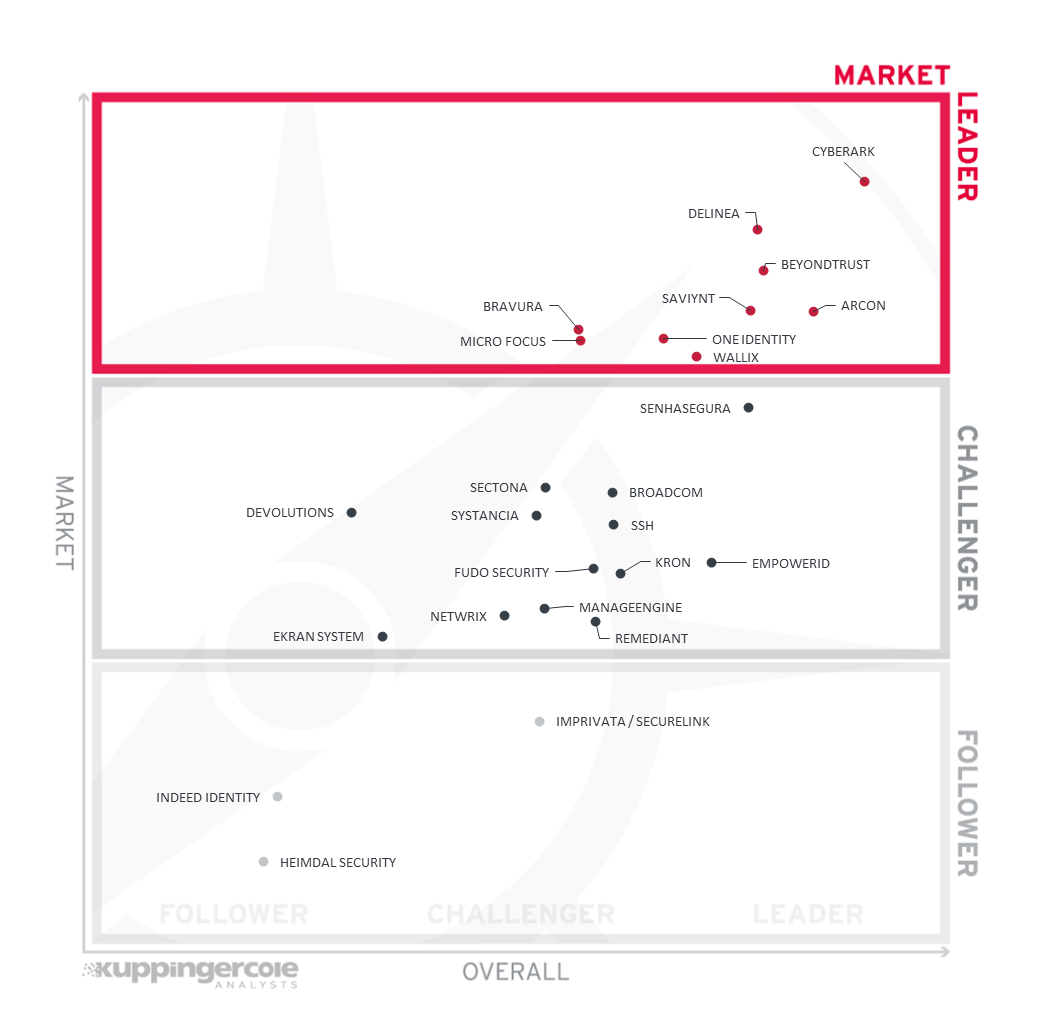
Figure 4: The Market Leaders in PAM
Market Leaders (in alphabetical order):
- ARCON
- BeyondTrust
- Bravura
- CyberArk
- Delinea
- Micro Focus
- One Identity
- Saviynt
- WALLIX
3 Correlated View
While the Leadership charts identify leading vendors in certain categories, many customers are looking not only for a product leader, but for a vendor that is delivering a solution that is both feature-rich and continuously improved, which would be indicated by a strong position in both the Product Leadership ranking and the Innovation Leadership ranking. Therefore, we provide the following analysis that correlates various Leadership categories and delivers an additional level of information and insight.
The first of these correlated views contrasts Product Leadership and Market Leadership.
3.1 The Market/Product Matrix
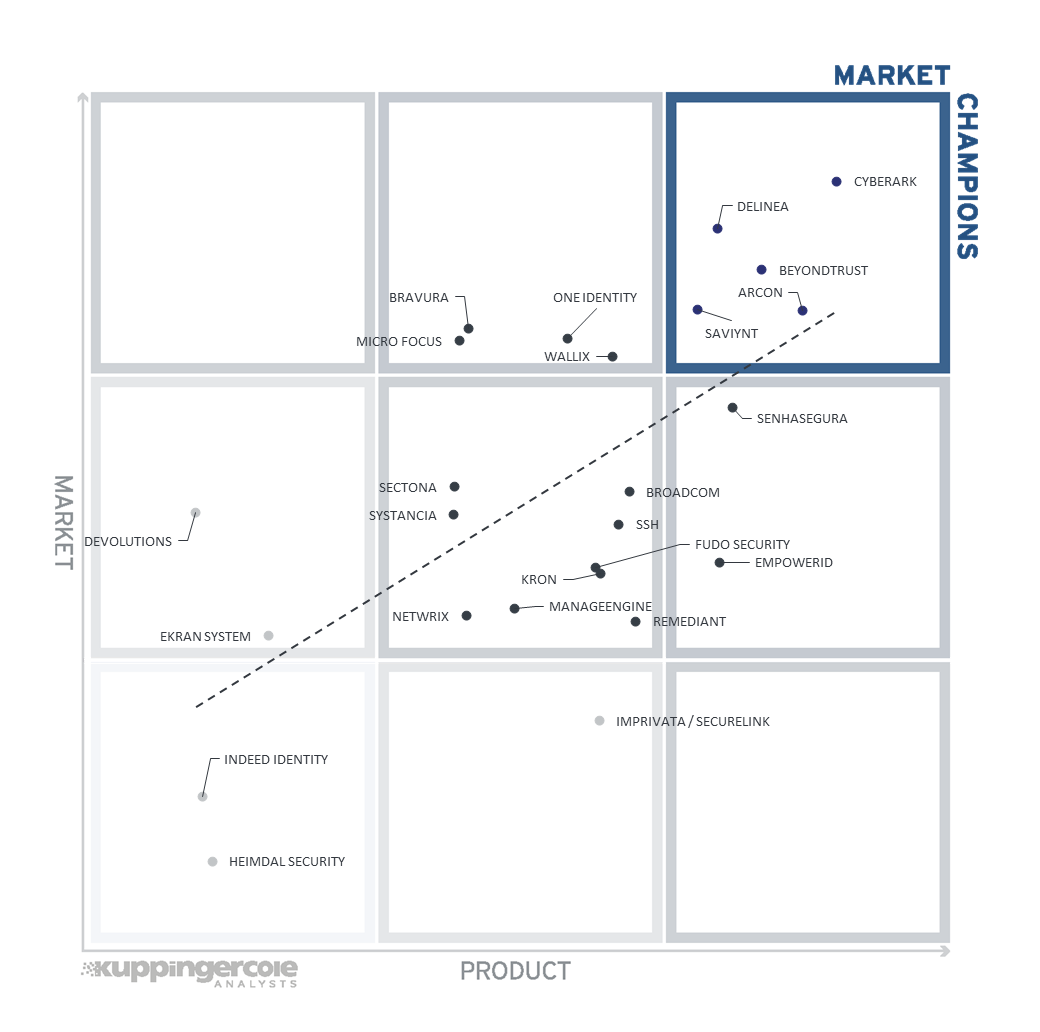
Figure 5: The Market/Product Matrix for PAM
Vendors below the line have a weaker market position than expected according to their product maturity. Vendors above the line are sort of “overperformers” when comparing Market Leadership and Product Leadership.
All the vendors below the line are underperforming in terms of market share. However, we believe that each has a chance for significant growth.
3.2 The Product/Innovation Matrix
This view shows how Product Leadership and Innovation Leadership are correlated. It is not surprising that there is a pretty good correlation between the two views with a few exceptions. The distribution and correlation are tightly constrained to the line, with a significant number of established vendors plus some smaller vendors.
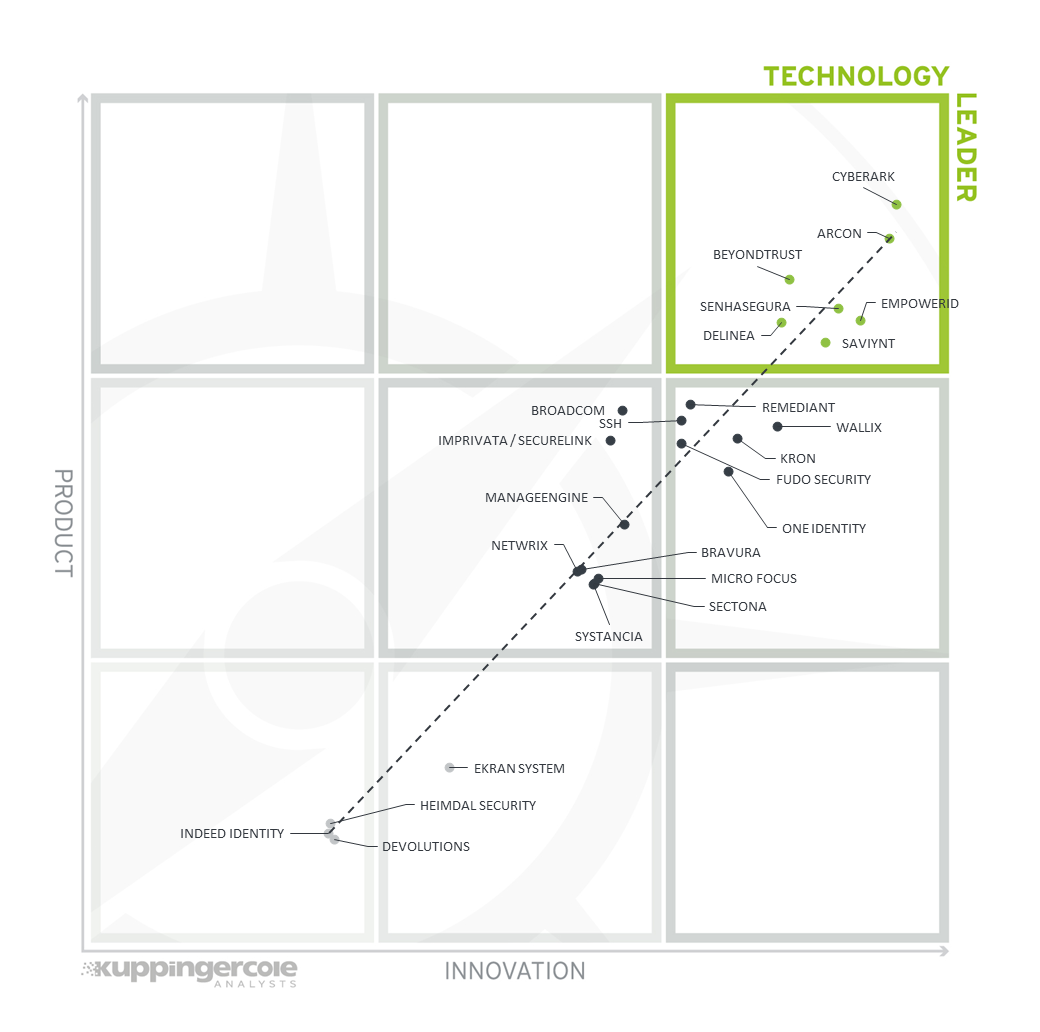
Figure 6: The Product/Innovation Matrix for PAM
Vendors below the line are more innovative, vendors above the line are, compared to the current Product Leadership positioning, less innovative.
3.3 The Innovation/Market Matrix
The third matrix shows how Innovation Leadership and Market Leadership are related. Some vendors might perform well in the market without being Innovation Leaders. This might impose a risk for their future position in the market, depending on how they improve their Innovation Leadership position. On the other hand, vendors who are highly innovative have a good chance for improving their market position. However, there is always a possibility that they might also fail, especially in the case of smaller vendors.
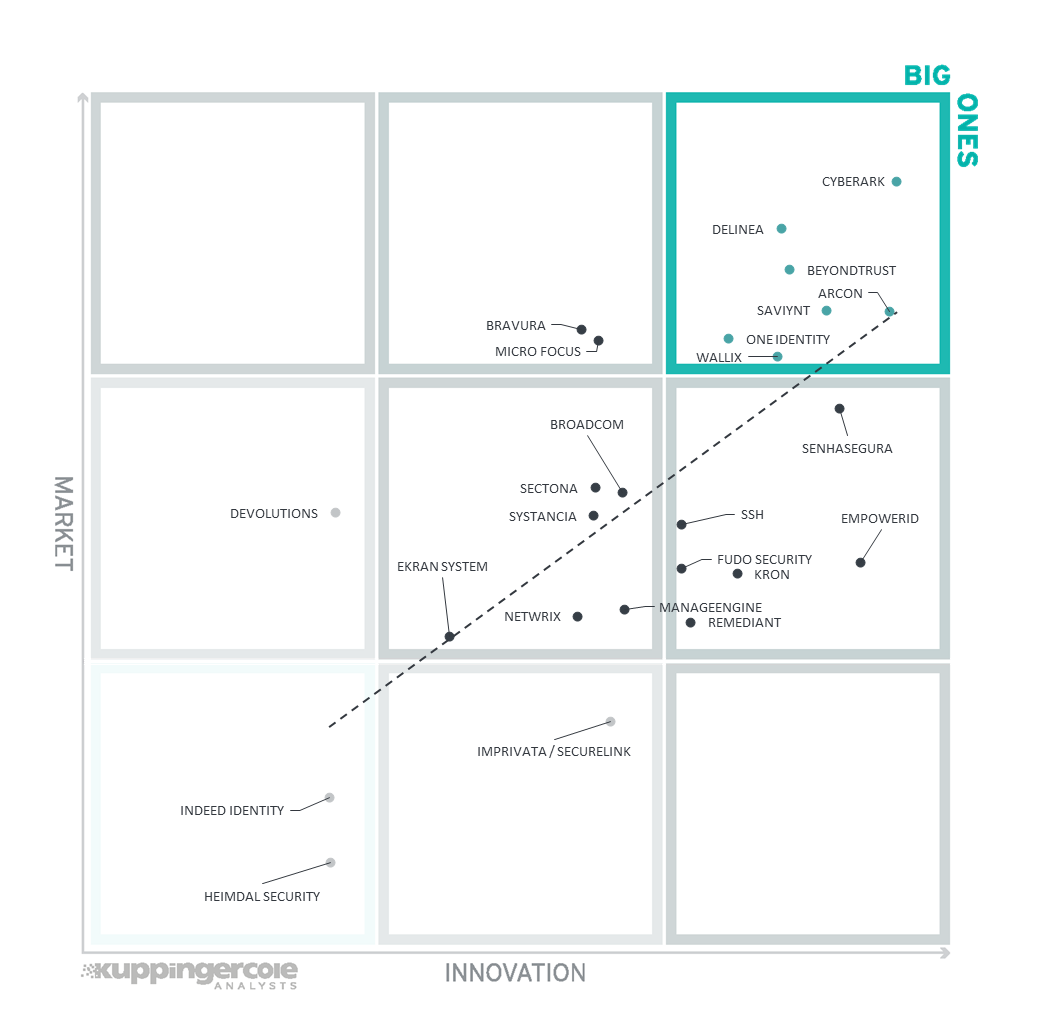
Figure 7: The Innovation/Market Matrix for PAM
Vendors above the line are performing well in the market as well as showing Innovation Leadership; while vendors below the line show an ability to innovate though having less market share, and thus the biggest potential for improving their market position.
4 Products and Vendors at a Glance
This section provides an overview of the various products we have analyzed within this KuppingerCole Leadership Compass on DREAM Platforms. Aside from the rating overview, we provide additional comparisons that put Product Leadership, Innovation Leadership, and Market Leadership in relation to each other. These allow identifying, for instance, highly innovative but specialized vendors or local players that provide strong product features but do not have a global presence and large customer base yet.
Based on our evaluation, a comparative overview of the ratings of all the products covered in this document is shown in Table 1.
| Vendor | Security | Functionality | Deployment | Interoperability | Usability |
|---|---|---|---|---|---|
| ARCON | |||||
| BEYONDTRUST | |||||
| BRAVURA (HITACHI ID) | |||||
| BROADCOM | |||||
| CYBERARK | |||||
| DELINEA | |||||
| DEVOLUTIONS | |||||
| EKRAN SYSTEM | |||||
| EMPOWERID | |||||
| FUDO SECURITY | |||||
| HEIMDAL SECURITY | |||||
| IMPRIVATA / SECURELINK | |||||
| INDEED IDENTITY | |||||
| KRON | |||||
| MANAGEENGINE | |||||
| MICRO FOCUS | |||||
| SENHASEGURA | |||||
| NETAND | |||||
| NETWRIX | |||||
| ONE IDENTITY | |||||
| REMEDIANT | |||||
| SAVIYNT | |||||
| SECTONA | |||||
| SSH | |||||
| SYSTANCIA | |||||
| WALLIX |
Table 1: Comparative overview of the ratings for the product capabilities
In addition, we provide in Table 2 an overview which also contains four additional ratings for the vendor, going beyond the product view provided in the previous section. While the rating for Financial Strength applies to the vendor, the other ratings apply to the product.
| Vendor | Innovation | Market Position | Financial Strength | Ecosystem |
|---|---|---|---|---|
| ARCON | ||||
| BEYONDTRUST | ||||
| BRAVURA (HITACHI ID) | ||||
| BROADCOM | ||||
| CYBERARK | ||||
| DELINEA | ||||
| DEVOLUTIONS | ||||
| EKRAN SYSTEM | ||||
| EMPOWERID | ||||
| FUDO SECURITY | ||||
| HEIMDAL SECURITY | ||||
| IMPRIVATA / SECURELINK | ||||
| INDEED IDENTITY | ||||
| KRON | ||||
| MANAGEENGINE | ||||
| MICRO FOCUS | ||||
| SENHASEGURA | ||||
| NETAND | ||||
| NETWRIX | ||||
| ONE IDENTITY | ||||
| REMEDIANT | ||||
| SAVIYNT | ||||
| SECTONA | ||||
| SSH | ||||
| SYSTANCIA | ||||
| WALLIX |
Table 2: Comparative overview of the ratings for vendors
5 Product/Vendor evaluation
This section contains a quick rating for every product/service we’ve included in this KuppingerCole Leadership Compass document. For many of the products there are additional KuppingerCole Product Reports and Executive Views available, providing more detailed information.
Spider graphs
In addition to the ratings for our standard categories such as Product Leadership and Innovation Leadership, we add a spider chart for every vendor we rate, looking at specific capabilities for the market segment researched in the respective Leadership Compass. For the Leadership Compass PAM, we look at the following eight categories:
- Just in Time
- Dashboard
- Analytics
- DevOps
- Data Governance
- Cloud Deployment
- Account Discovery
- High Availability
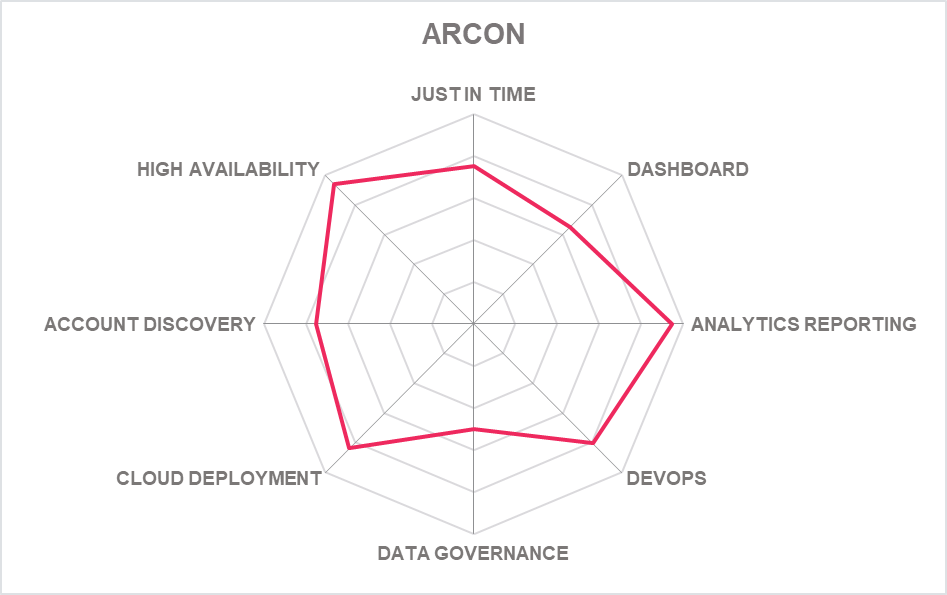
5.1 ARCON – Privileged Access Management Platform
Founded in 2006 and based in Mumbai (India), ARCON offers its Privilege Account Management Suite to manage privileged access across various delivery models. ARCON takes a reliable modular approach to PAM, and software is offered in software, virtual and physical appliances, and PAM as a Service (PAMaaS) option.
ARCON makes good use of a browser-based approach. During session management, for example, controllers can open multiple privileged sessions as tabs, waiting for approval in several at a time – saving time and resources.
Authentication is by SSH key and not passwords and authentication take place on the initial login page to the ARCON system. The auto-onboarding tool of ARCON PAM can be integrated with Microsoft AD, AWS, Azure Active Directory and GCP for onboarding all privileged accounts and services. The auto-onboarding solution - both AD scanner and Network Discovery Utility can run near real-time syncing of data from AD. The modern interface mixes the best of consumer tech design with neat touches such as "My Apps" for Admins. The ARCON EPM module can also control what users do at the endpoint and is now based on JIT processes. Data Intellect". This component enables the classification of data using AI/ML, itemization of the exposed data, categorization of the critical data along with giving a complete understanding of "where" and "what" of data. It allows one to have a complete track of where all important the important data lies in the organization.
ARCON My Vault is offered as a standalone option for those desires secret vault for different infrastructures. The solution is based on a microservices framework and is built for the cloud (it can also be installed on-premises for PAM customers). The Vault has advanced features like onboarding user groups, tagging businesses, workflow, Just-in-Time access to Secrets, Keys, Certificates, Files, etc. Further, users can deploy role-based access for sharing, downloading, viewing, or transferring files and secrets – a unique and useful capability. It also provides administrative users managing servers the ability to transfer files from one machine to another without having to go through interactive access in PAM without knowing the passwords and full RBAC controls
ARCON has now developed a unique Offline Vault capability as an extension of the PAM solution and is designed to assist remote workers and those on the road. An Offline Sync button ensures that all the devices the user has access to will sync with a highly secured local vault on the end user machine (endpoint). Once the vault is synchronized, the user can carry their laptop, connect to the console of the devices they have access to, and simply click to start a session in the PAM app. Credentials are auto injected and the session is now monitored, without the user having to see or know the passwords. Session logs are stored locally and synced centrally when the endpoint comes in the network.
ARCON Digital PAM is a PAM solution for Non-Human Identities, leveraging native application attributes and role-based access controls to authenticate applications and containers. It can manage and pass credentials securely to validated containers DevOps tools and automated systems and clusters when required.
ARCON has launched a new design for its administrative console and this all modules will be migrated to this new design theme. The theme is carefully designed to meet the standard requirement of WCAG Standards. ARCON says the entire administrative console of the product has been process re-engineered. A full Management Portal for AWS is planned increasing ARCON’s compatibility with cloud infrastructures and dynamic access.

| Ratings | Security |  |
| Functionality |  |
|
| Deployment |  |
|
| Interoperability |  |
|
| Usability |  |
| Strengths |
|
| Challenges |
|
| Leader in |  | 
|  | 
|
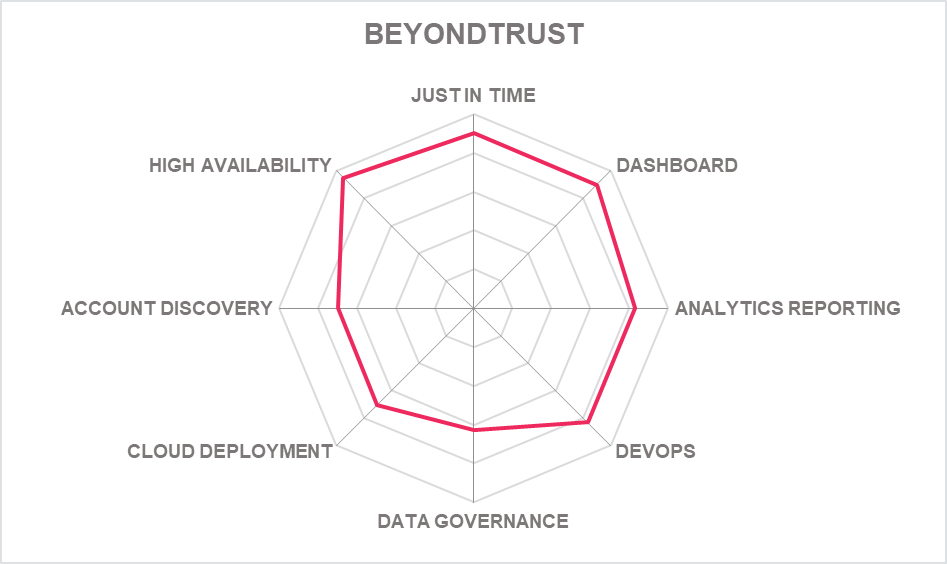
5.2 BeyondTrust – PAM Portfolio
BeyondTrust has continued to refine its portfolio of PAM products which now includes the Password Safe and DevOps Secrets Safe products, Endpoint Privileged Management (EPM) tools (for Windows, Mac, Unix and Linux), AD Bridge, the Remote Support and Privileged Remote Access products, and the new Cloud Privilege Broker product. There is also BeyondInsight, a separately available analytics package platform. All now benefit from an upgraded and consistent UI – in line with market trends.
This collection makes it one of the most comprehensive on the market, covering all the recognized functionalities of a PAM suite and takes account of the global interest in securing Privileged Access for home working. BeyondTrust PAM can be deployed in the on cloud, as hybrid and on-premises. SaaS options with feature parity are available for every key product in the portfolio. BeyondTrust continues to innovate and add capabilities. Password Safe has a continued focus on ease of use with an updated UI/UX interface to support core operations like onboarding new secrets and managed systems and can also help organizations bring systems that are disconnected or intermittently connected to the network under management. DevOps Secrets Safe has an updated UI/UX interface with expanded reporting depth and new SaaS deployment options.
Also targeted at the cloud is new cloud security management capabilities were added with the CIEM focused BeyondTrust Cloud Privilege Broker (CPB) application, designed to manage entitlements across multi-cloud environments. CPB sits on the BeyondInsight platform, providing current customers with a familiar interface. An advantage for existing BeyondTrust customers is full compatibility with the BeyondInsight platform, providing integration across the full BeyondTrust PAM suite. For Endpoint Privilege Management, there are now new deeper integrations with ServiceNow for exception handling, VirusTotal for analytical insight, SIEM tools and continual evolution of our MFA and Azure AD integrations, allowing the use of new MFA providers and more use cases of AAD. The Advanced Parent Tracking feature protects against malware that evades detection through Windows parent and child process hierarchies, an emerging approach for malware strains. A new SailPoint IGA integration brings a welcome strengthening of the platform’s Identity management capabilities.
Other innovations include the launch of a granular roles & permissions system in the SaaS EPM management console, allowing customers to segment administration of their estate with fine-grained controls. BeyondTrust provides third- party access with a self-registration portfolio and simplified management tools for third party vendors. BeyondTrust is offering vendors greater autonomy over PAM while keeping entitlement and resources secure. Finally, the new look Cloud Privilege Broker (CPB) has been redesigned for managing cloud access risk and governance of entitlements in hybrid and multi cloud environments.
A future release will guide users to remove standing privileges and assign entitlements for a specified window of time, to accomplish only specific tasks. While BeyondTrust in its current incarnation remains an undoubted leader for PAM, big changes are promised for beyond 2022. A new platform will consolidate data streams from multiple BeyondTrust products and apps and enrich data streams in real time in a centralized, high performance data store. The new platform will use APIs for smoother and wider integrations, AI/ML algorithms to deliver prescriptive analytics and descriptive analytics with actionable insights available. Exciting times ahead.

| Ratings | Security |  |
| Functionality |  |
|
| Deployment |  |
|
| Interoperability |  |
|
| Usability |  |
| Strengths |
|
| Challenges |
|
| Leader in |  | 
|  | 
|
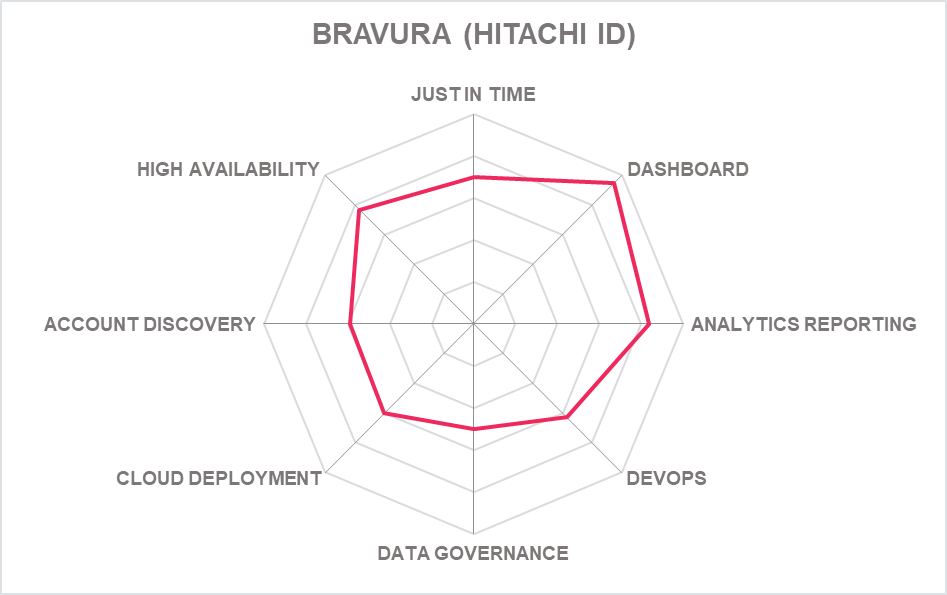
5.3 Bravura Security (formerly Hitachi ID) – Security Privilege
Bravura Security was formerly known as Hitachi ID Systems, Inc until a very recent acquisition by the Canadian investment specialists Volaris Group. Bravura Security Privilege is part of the Bravura Security Fabric product group that also includes Bravura Pass, Bravura Identity and Bravura Safe. Buyers can mix and match modules to tailor a solution to fit the needs of their organization as all are fully compatible.
Bravura Privilege relies on proven password and vault technology, which also addresses some of the shortcomings of passwords with PAM. It automatically replaces shared and static passwords assigned to privileged accounts with periodically new and random values based on password policy controls set by the organization. It can also enforce multiple scheduled or event-triggered password policies on fixed IT assets, laptops, and virtual machines. This backed up with sensible and robust data protection tools including active-active architecture that can replicate data sets in real time across all geographies for HA and disaster recovery purposes. Data at rest and in transit is encrypted using AES 256 encryption keys unique to each customer. Bravura also offers multiple copies of the vault and option to store other files in those vaults.
Bravura Privilege retains its strong discovery capabilities to find all accounts, groups and services and regular auto discovery based on policy is possible. In addition, system data can be analyzed, and policies and credentials set for resources available to identities, and the right policies to attach to each one. Automated discovery routines can be set by admins, also based on policies, and designed to enable more efficient scaling and reporting.
In terms of more dynamic access Bravura Privilege is need of a little catch up in terms of DevOps and cloud entitlement management, JIT access is available but still takes quite a bit of administrative work to limit privilege access for identities and native Zero Standing Privilege (ZSP) with passwordless access is still some way off. Bravura is hardly alone in this, however, and the company is committed to developing the platform via Open Data Protocol APIs to evolve the user experiences with Bravura Pass, Identity, and Privilege components which we hope will see a shift to more dynamic, cloud native capabilities soon. To that end, Bravura Safe is already built on top of AWS ECS serverless technology to automatically scale as demand grows.
Bravura has continually offered robust and reliable PAM tools that lacked some cutting edge and the there was a feeling that technical development and improved market presence were frustrated. A change of ownership, new investment and focus may now speed further development.

| Ratings | Security |  |
| Functionality |  |
|
| Deployment |  |
|
| Interoperability |  |
|
| Usability |  |
| Strengths |
|
| Challenges |
|
| Leader in |  | 
|  | 
|
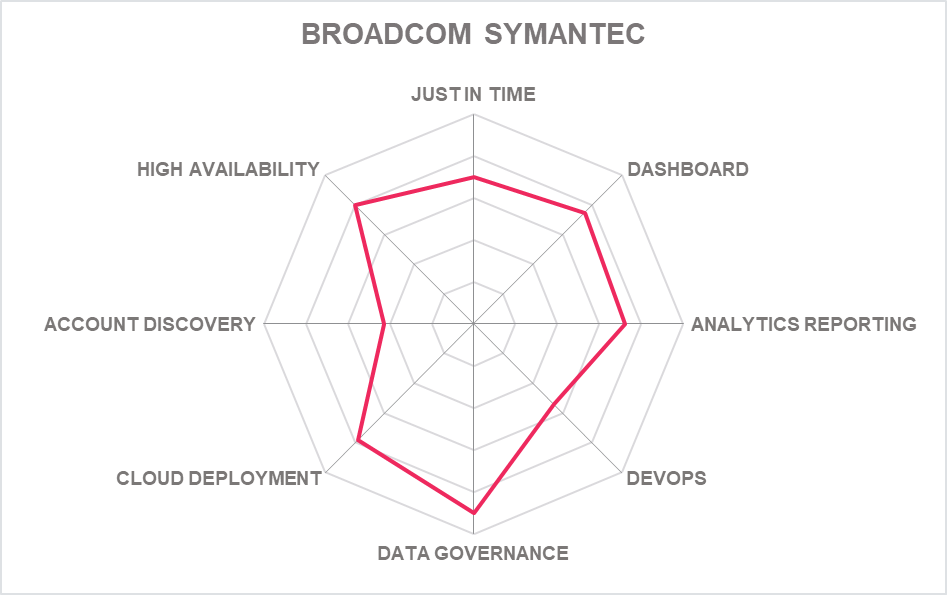
5.4 Broadcom – Symantec PAM
Broadcom has now rationalized all its identity products into the Identity Management Security Division of Broadcom Software, including its PAM platform marketed as Symantec PAM.
The solution is designed well for hybrid environments with AWS and Azure support and Broadcom claims its appliances can be stood up very quickly, with auto discovery of privileged accounts getting basic PAM up and running in 2- 3 days. The product is available as a rack-mounted, hardened hardware appliance, Open Virtual Appliance (OVA) Amazon Machine Instance (AMI) or a Virtual Hard Disk (VHD) for Azure. Yet, there is still no SaaS version and no sign of any new CIEM capability, which is another challenge.
The software compartmentalizes high-risk users, alerting, remediating, tracking, recording, and reporting on all user activities inside the T infrastructure. Administrators, application developers, vendors, and technical contractors can securely access critical IT resources from inside and outside the organization without gaining a footprint on the network. There is now full integration with Symantec Secure Access Cloud ZTNA solution
Broadcom has introduced light-weight desktop agent that allows users to connect to target systems using privileged account without having to log into the PAM user interface directly. Users can use their own tools for connecting and PAM will manage the credentials behind the scenes.
Other capabilities are open REST API's (including SCIM), CLI's and several out-of-the-box integrations with Identity and Access Management solutions, SIEM solutions, Service Desk solutions etc. The PAM Server Control offers an agent-based architecture to intercept control and restrict commands at OS Kernel level. It is notable for its fine-grained access control able to block Root access to a file or give one specific account access to a file or service. Policies can be upgraded through the central console. The Threat Analytics engine delivers advanced threat analytics leveraging machine learning techniques for automated detection of risky privileged behavior.
The affinity with CA's former IAM products remains, and Symantec's customer history shows that this PAM platform can scale to multiples of 100k of devices and users and is at home in hybrid IT environments. A solid choice and one that may now flourish under the Symantec Enterprise Security umbrella if further IAM integration plans come to fruition – as with other vendors, marrying IAM and PAM is seen as the next step forward. We would like to see much more for DevOps, and CIEM compatible tools introduced within the next 12 months. Broadcom offers a tried and tested PAM one stop solution that offers 100% of the desired capability options – if not yet a technology leader in all of them.

| Ratings | Security |  |
| Functionality |  |
|
| Deployment |  |
|
| Interoperability |  |
|
| Usability |  |
| Strengths |
|
| Challenges |
|
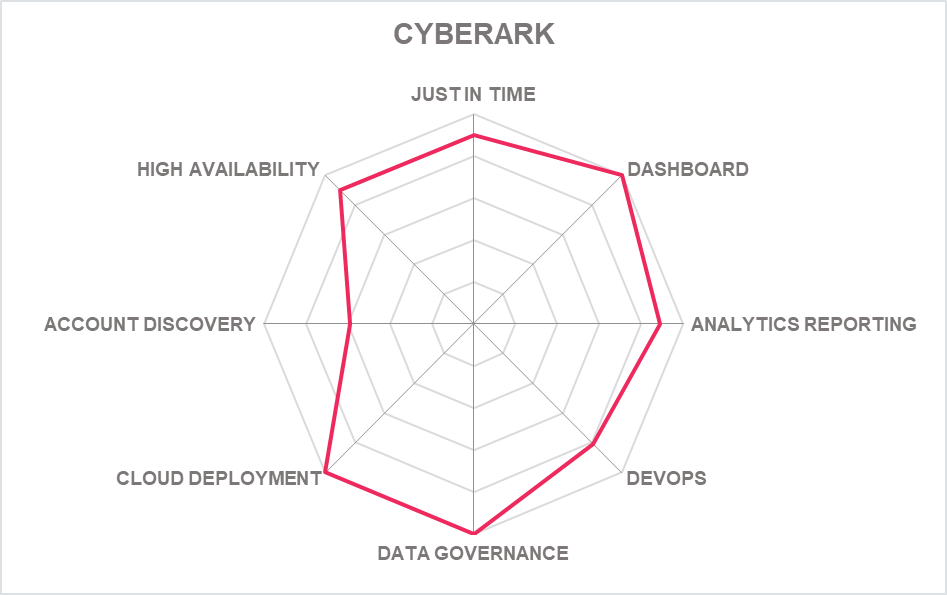
5.5 CyberArk – Identity Security Platform
Headquartered in Israel and the US, CyberArk has a mature PAM provider been in the market since 1999. It has continued to add technical functionality to its broad suite of products in response to changing market demands.
The full CyberArk PAM portfolio includes CyberArk Privileged Access Manager available as self-hosted or as PAMaaS (CyberArk Privilege Cloud); its PAM for DevOps product, Conjure Secrets Manager; CyberArk Remote Access for vendors, third parties (Vendor PAM) and privileged employees from remote locations; and CyberArk Endpoint Privilege Manager (EPM). CyberArk EPM removes local administrator rights from endpoints and offers temporarily elevated privileges for specific tasks in real-time.
More boldly, perhaps, Cyber Ark has started to rebrand the business around this its enhanced product portfolio as an Identity Security vendor, encompassing IAM, PAM and Cloud management. This messaging may take some ironing out but get it right and it will be a canny move to stay ahead of growing interest in the PAM market from IAM vendors. It also dovetails well with KuppingerCole's Identity Fabric model for organizations.
In Conjur, its DevOps product, segregation of data between different environments using the same vault is now possible by synching different secrets to different Conjur Enterprise instances. There is also now native authentication support for Azure and Google Cloud Platforms. Cloud Entitlements Manager, a new SaaS offering introduced in November 2020, uses AI-powered detection and remediation of hidden, misconfigured, and unused permissions across an organization's cloud environments. This move demonstrated CyberArk’s ability to read the market ahead of many of its rivals, and one of the reasons it topped the KuppingerCole DREAM Leadership Compass.
CyberArk also offers in depth analytics, session management, elevation management and AAPM technologies across its suite of products. The products on offer here remain the benchmark in integrating new capabilities with tried and tested technology while keeping up with new challenges such as remote access, DevOps, cloud and identity management integration.
CyberArk has increased its coverage of target systems for least privilege enforcement by improving EPM support for MacOS, introducing support for Windows ARM and Linux. Cloud Entitlements Manager also helps extend least privilege as organizations adopt new cloud platforms and modern identity frameworks for policy targeting. Secrets Manager introduced JWT based authentication for OpenShift and Kubernetes containers and support for SNI certificates – to be able to authenticate workloads running on these Cloud platforms and eliminating the “secret zero problem”. CyberArk has introduced Dynamic Privileged Access to address Just-in-Time access requirements by providing ephemeral access to cloud and on-premises infrastructure.
CyberArk continues to innovate in with new capabilities including Dynamic Privileged Access and Cloud Entitlements Manager. Dynamic Privileged Access provides Ephemeral privileged access to reduce address standing access and associated risks. Cloud Entitlements Manager with Dynamic Privileged Access and implements least privilege for human identities and roles/service accounts used in serverless workloads by using Cloud Entitlements Manager’s with code scanning capabilities, which recommend a least privilege policy based on the used API resources.

| Ratings | Security |  |
| Functionality |  |
|
| Deployment |  |
|
| Interoperability |  |
|
| Usability |  |
| Strengths |
|
| Challenges |
|
| Leader in |  | 
|  | 
|
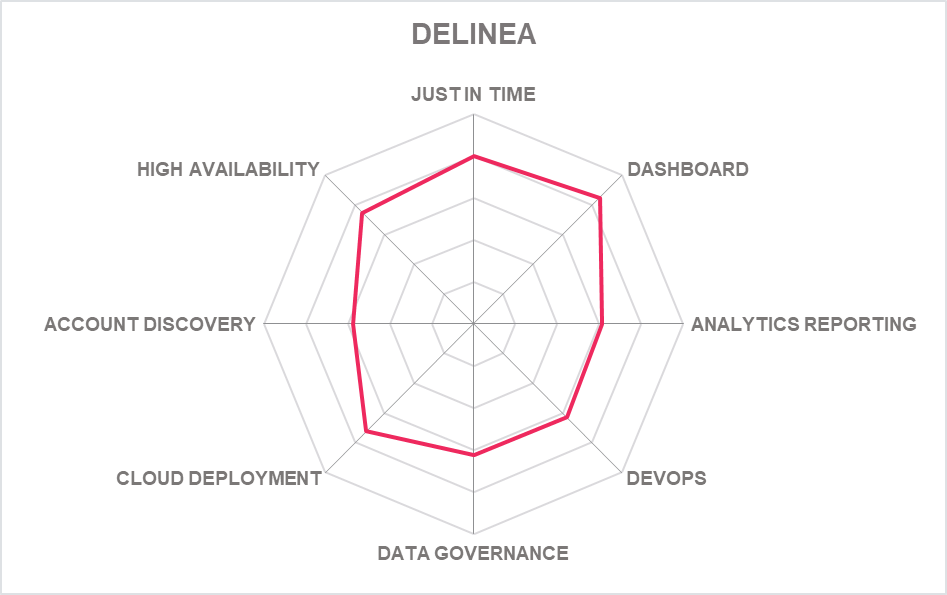
5.6 Delinea – PAM Suite
Delinea is the brand for the merged entities of Thycotic and Centrify, and is now based in Redwood City, California. After a period of consolidation in the business, the company has restructured its PAM line up relative to the strengths of former Centrify and Thycotic Software to eradicate capability overlap and play to strengths.
The full line up of Delinea’s products and services is now listed as follows: Delinea Secret Server, Delinea Server Suite, Delinea Cloud Suite, Delinea Privilege Manager, Delinea DevOps Secrets Vault, Delinea Account Lifecycle Manager, Delinea Privileged Behavior Analytics, Delinea Connection Manager. All are available for On Premises or SaaS deployment and management except for DevOps Secrets Vault (SaaS only). As part of the continuing licensing deal with IBM, Delinea Secret Server, Privilege Manager, Server Suite, DevOps Secrets Vault, Account Lifecycle Manager and Connections Manager are also available packaged through IBM Security Services. Cloud hosted offerings such as Secret Server Cloud feature automated capacity management to scale available resources according to demand.
For buyers this means that Delinea now has the strength of Centrify’s PEDM capability combined with the recognized capacity of Thycotic’s Secret Server vaulting technology. But what else does the new brand offer? It’s a mixed picture.
The Threat Analytics Service, which uses machine learning to identify anomalous behaviour in real time, is now engineered to work with Secret Server. This activates policies for users who are accessing the vault, initiating a privileged session, or checking out a password. Delinea has plans to extend existing Privileged Behavior Analytics to encompass server PAM use cases and cloud entitlements, facilitating detection of anomalous activity on servers and over privilege in cloud infrastructures. We would have liked to see this more currently, however.
Delinea provides multiple options for access to privileged sessions. Users can choose from direct in the application, support for 3rd party
session management tools, an endpoint session management client and web-based RDP and SSH session tools. Web browser plugins for automatic
credential filling on web UIs and mobile app providing access to credentials and integration with mobile OS credential management complete the
picture.
Delinea Privilege Manager is an agent based EPM solution for Windows, Mac, and Linux endpoints that supports extensive EPM capabilities including
application control and privilege elevation (available on-premises or as a SaaS-hosted solution in Azure).
The current iteration of Delinea is pretty much what a merger of two major PAM vendors might deliver - a more complete set of traditional PAM capabilities. There is some effective consolidation but overall, this is a package that has effectively suffered from a lack of key development while the merger was going through. We can’t help but wonder where Thycotic and Centrify might have been without the merger. It remains a powerful platform in 2022 but much has been set aside for the future.
This includes improved security for access to Kubernetes pods, better CIEM and remote access tools. But much will wait until a brand-new platform is developed to support all existing modules from Delinea expected in 2023.

| Ratings | Security |  |
| Functionality |  |
|
| Deployment |  |
|
| Interoperability |  |
|
| Usability |  |
| Strengths |
|
| Challenges |
|
| Leader in |  | 
|  | 
|
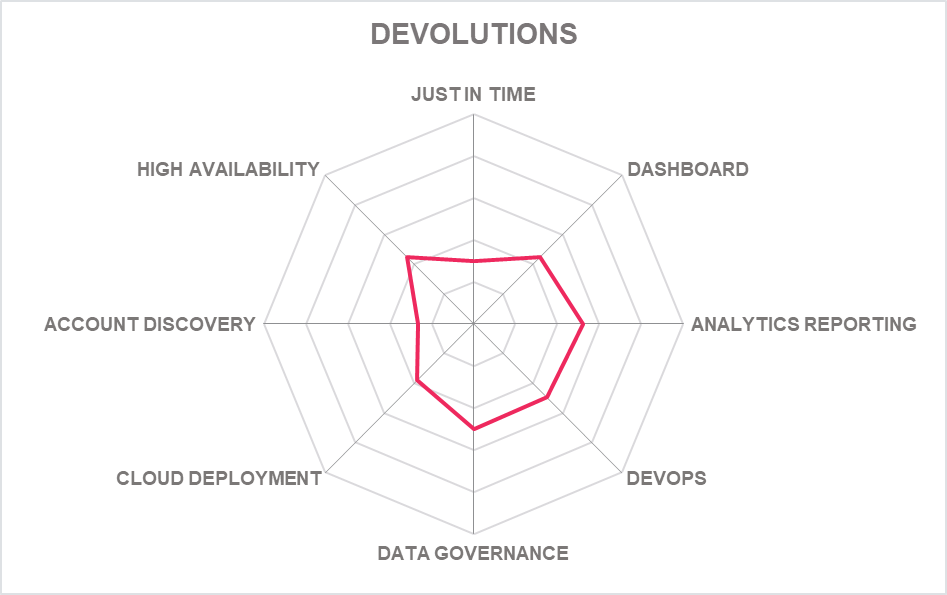
5.7 Devolutions – Server Team, Enterprise and Platinum Editions
Founded in 2010, Canadian firm Devolutions started with its Remote Desktop Manager product aimed at SMBs. It has since added PAM capabilities to its portfolio with the Devolutions Server There is also the Devolutions Password Hub, a password manager also aimed at smaller businesses and Devolutions Gateway for JIT access to internal or external segmented networks. All three products can integrate with each other depending on need.
Devolutions Server offers the essential capabilities such as a shared password vault, which can integrate with Microsoft Active Directory and can be hosted centrally. It also offers account discovery and secure remote access. But for a package that is created with SMBs in mind it has several enterprise capabilities including session recording and playback, automated password check in/check out and SSO. It lacks others, however: privileged escalation, and privileged task management for example, but does support JIT access (via Devolutions Gateway) and One Time Passwords (OTP) – good to see.
It remains strong on account discovery focusing on identifying privileged (and specifically, shared) accounts across various systems in a network and putting them under control. Together with the ability to remotely manage target systems running various operating systems such as MacOS, Windows, and Linux, and the password vaulting and management capabilities, this forms a PAM solution covering the essential capabilities required by SMBs, while remaining lean and relatively easy-to-use. The platform supports 2FA, AES-256 encryption, encrypted communications over HTTPS using TLS, IP restriction and time-based, Role-based (RBAC), DAC, Application-level restrictions.
For 2022, Devolutions remains focused on ease of use and PAM essentials for smaller businesses with an improved Devolutions Gateway platform to provide JIT access. This now supports OAuth and support for Okta, better code management, support for unmanaged accounts and ticketing support via Atlassian Jira. There is now also checkout approval available on the Devolutions mobile app.
While still very much a lean SMB PAM platform, deployment has been simplified in the last 12 months and there is good flexibility available in the capabilities that buyers can choose, especially when partnered with other Devolutions software. However, there is still no cloud or SaaS option of the Server product, and we hope to see that in coming iteration.

| Ratings | Security |  |
| Functionality |  |
|
| Deployment |  |
|
| Interoperability |  |
|
| Usability |  |
| Strengths |
|
| Challenges |
|
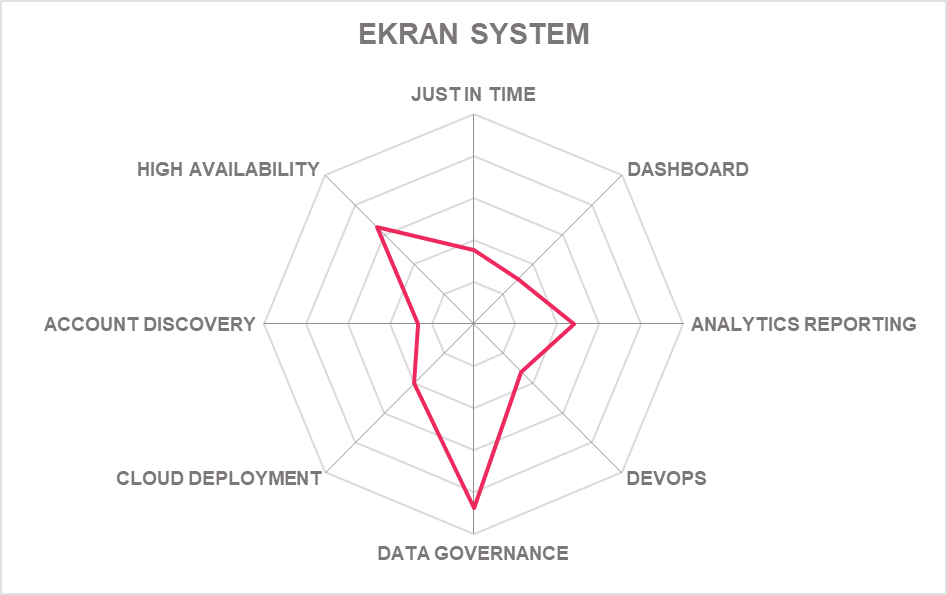
5.8 Ekran System – Platform
Ekran System is based in Newport Beach, California and specializes in User and Identity Management solutions. Ekran System also provides a PAM solution within a single endpoint agent. This includes privileged access and session management via a jump box, password management, request access workflow and two-factor authentication. It supports both cloud and on-premises deployments.
In the last year Ekran has added some more enterprise focused features with a new dashboard that monitors multiple sessions, a HA mode, load balancer and multi-tenancy support. None of this is revolutionary, but it does mean that buyers attracted to Ekran’s approach to PAM can now scale more effectively as infrastructure expands. A new real-time alert window and full integration with Microsoft Power BI also add more ballast to the platform.
Other improvements include the Anonymizer (Compliance with GDPR), support of SELinux, full, password checkout, tree view for secrets (same as folders), updated dashboards and an updated session player. The company is currently developing a SaaS platform, which will be welcome to many SMB buyers.
For development and integration purposes there is some API support including application credential brokerage, ticketing system integration, and provision of monitored information via API; more API support would be welcome if Ekran System is to compete against the leaders in integration.
Session monitoring and recording is well taken care of. Video recordings are indexed with multilayer metadata including names of active applications, titles of active windows, websites (URLs) visited, keystrokes typed, commands and scripts executed, and devices connected. A single Ekran System Terminal Server Client can be installed on a jump server to monitor all sessions that come through it. The trigger rules for alerts can be set and modified by the customer.
There are some elements of Artificial Intelligence (AI) in play. The Ekran User and Entity Behaviour Analytics (UEBA) engine can detect a hacker with stolen credentials through self-learning techniques. The working hours of a genuine user are scanned, and a formal baseline created from which to compare anomalous or unusual behaviour. The company has plans to develop this with new behavioral factors for baselining. We look forward to more development in this exciting area.
Ekran has been busy adding much needed improvements to its platform and it now is a much stronger player which adds capabilities to its existing strengths of good design, simplicity, and ease of use.

| Ratings | Security |  |
| Functionality |  |
|
| Deployment |  |
|
| Interoperability |  |
|
| Usability |  |
| Strengths |
|
| Challenges |
|
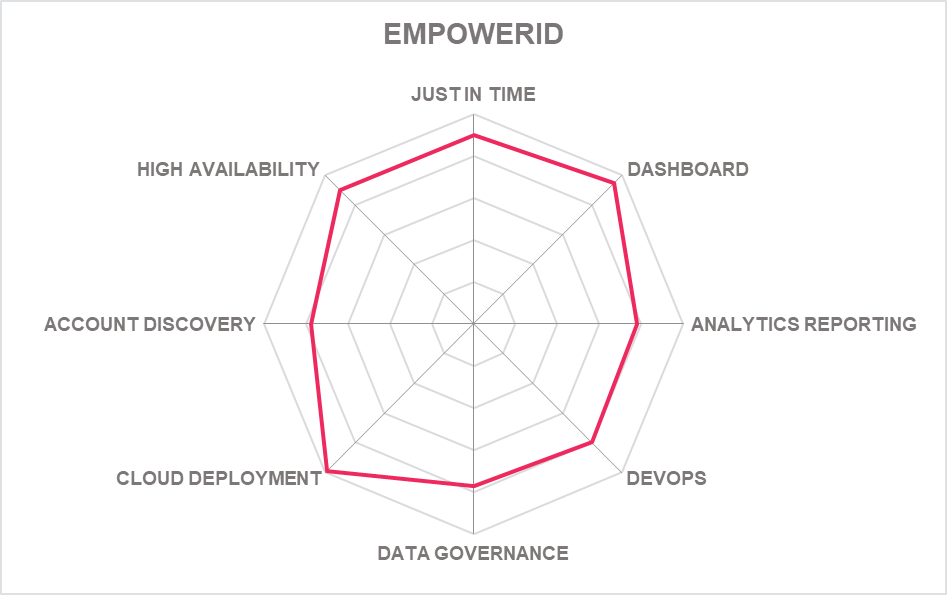
5.9 EmpowerID – Platform
Based in Ohio (US), EmpowerID offers several products within its broader IAM portfolio, including EmpowerID Privileged Access Management (PAM). All applications within the portfolio run as SaaS, and EmpowerID software offers fully managed services. The only on-prime component is Cloud gateway on Win 10/11 - this creates the credentials and keys.
Largely built on top of Microsoft technology, EmpowerID offers integration and performance benefits for Microsoft-centric organizations, particularly for existing customers of its user provisioning and identity governance products.
The product is completely workflow based. A set of 1000 ready-made workflows ship with the product to get started, and more can be added through simple drag and drop creation in Workflow Studio. It uses conventional vault technology, which hides passwords from users via RDP, SSH or web browser SSO. MFA support is through YubiKey Universal 2nd Factor Authentication, Duo Push, knowledge-based authentication (Q&A), and an OATH token server for issuing one-time password tokens.
EmpowerID has further developed its investment in Workflow Studio for 2022 with support for Microsoft Adaptive Card now added, which simplifies UI development. Further integration with Microsoft tools allowing users to create their own bots, supported as micro services in Azure. Bots can be configured to find users with too much privilege or garbage JIT access. The overall UI has been further optimized for mobile devices. EmpowerID is the most user customizable of all PAM platforms and should be commended for further adding bridging low code principles and knowledge levels that will support non-expert development.
Full PAM is available for DevOps and the Session Manager Architecture is completely broken out into microservices and fully containerized. There is a standards-based native Identity Provider built into the platform that provides SSO to cloud applications directly from a menu in the dashboard. Other IDPs are supported, and multi- factor authentication can be configured in addition using Azure, Duo, OAuth and mobile-based MFA apps. EmpowerID’s expertise in identity management make this a flexible access tool for DREAM.
EmpowerID has added an Eligibility Policy Engine which manages what users may see and request and which roles and resources in the enterprise can again access. Eligibility policies can be applied to users by query, role, group, or other criteria, to target who receives which policies. MFA support is through YubiKey Universal 2nd Factor Authentication, Duo Push, knowledge-based authentication (Q&A), and an OATH token server for issuing one-time password tokens
A new microservice called My Tasks provides a consumer grade UX for request and to do item tracking. My Tasks was designed to work with EmpowerID's new Business Request approval flow engine which supports multi-level approvals.
The dashboard at the heart of EmpowerID is comprehensive in scope and does more than just open access to cloud services. Other key capabilities include ML supported role mining with automatic cleanup of roles, display of rights granted to roles and the security impact these may have on the organizations. Business functions can be mapped to Azure Groups, for example, purchase Order functions. Whole groups can be switched to JIT access if the role is considered high-risk or optimized for Least Privilege Access – from an IAM background EmpowerID is developing new approaches to PAM.

| Ratings | Security |  |
| Functionality |  |
|
| Deployment |  |
|
| Interoperability |  |
|
| Usability |  |
| Strengths |
|
| Challenges |
|
| Leader in |  | 
|  | 
|
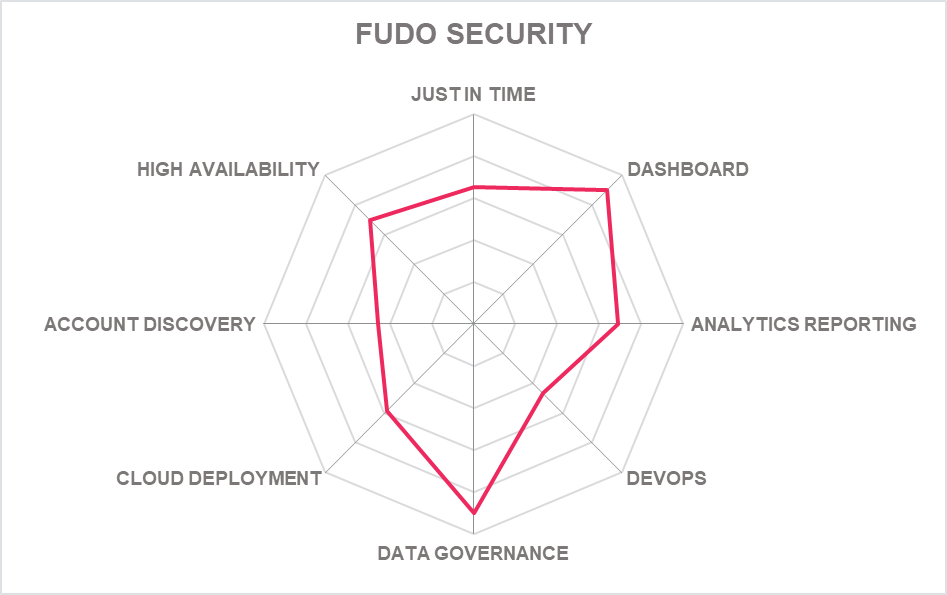
5.10 Fudo Security – Fudo PAM
Fudo Security, with offices in California and Poland was founded in 2004. It offers Fudo PAM as its primary PAM product in the market. Fudo Security is used across the North America, Europe. Asia and Middle East markets.
Fudo PAM has a modern, crisp interface and allows customization with drag and drop resizable tiles available. The same customization can be used for data presentation, useful for reporting and behaviour pattern management. Fudo PAM is an agentless, all-in-one solution, deployable mostly as a virtual appliance supporting VMware, AWS, Microsoft Azure and Google Cloud. Fudo PAM can be also offered as a SaaS and in the MSP model by partners.
For end users, the User Access Gateway portal provides easy access to servers – the user is presented with a list of servers in one place, and a privileged session state can be initiated by pressing the "play" button - a thoughtful touch and one that adds greater efficiency to PAM in digital environments.
Fudo Security has used AI used to detect biometric anomalies such as unusual mouse or typing movements within the CLI or dashboard components. The use of Machine Learning has been enhanced further with new PUBA capabilities. Fudo's latest release enables existing systems to build users and system usage profiles based on continuous analysis of behaviour patterns and anomalies. Password Management offers password changes through pre-defined scripts and in-house plug-ins can be used to automate password management.
Fudo PAM supports SIEM including ArcSight and Splunk platforms. It’s well thought out interface and AI tools that can detect unusual behaviour and suspicious sessions will appeal to organizations of all sizes looking for improvements in security. Analyze mouse moves, semantics, etc. – above average detection of someone taking over a laptop,
We would like to see more development in terms of capabilities and native support for cloud and DevOps such as support for tools such as Jenkins. And also, more for CPEDM. It does good support AAPM for application accounts and API support for good range of programming language AAPM connects with User Access Gateway over TLS, there are two options: reading the password or OTP that connects without sharing real password
Development items include a fully developed SaaS version operated by Fudo tailored towards cloud and multi-cloud environments and cross platform support for Kubernetes, containerized apps and cloud services platforms. Of perhaps greater significance will be full JIT access from the Fudo mobile app.

| Ratings | Security |  |
| Functionality |  |
|
| Deployment |  |
|
| Interoperability |  |
|
| Usability |  |
| Strengths |
|
| Challenges |
|
| Leader in |  | 
|  | 
|
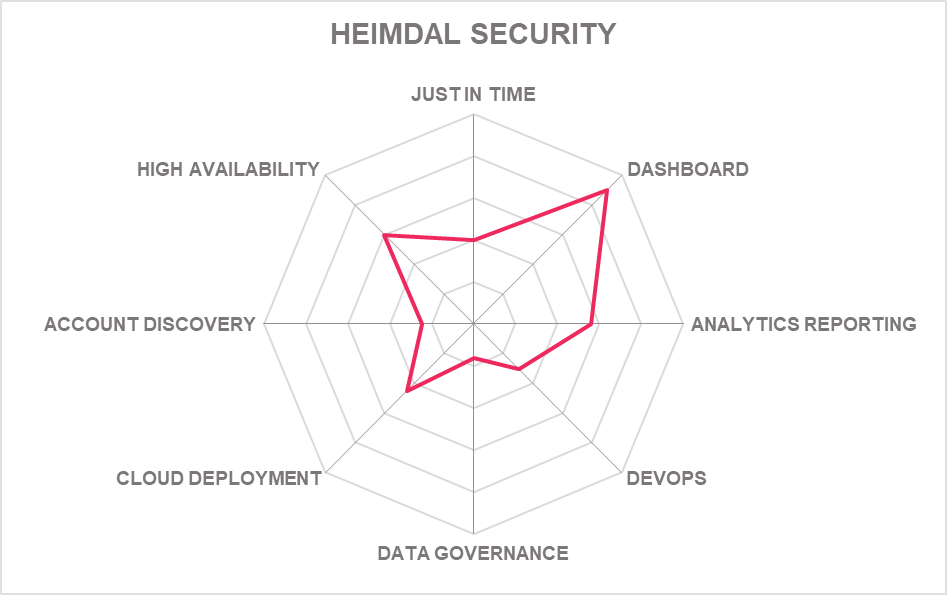
5.11 Heimdal Security – Privileges & Application Control
Heimdal is a security vendor based in Copenhagen, Denmark. It sells various security software products including this PAM tool which focuses on endpoint privileged session management and escalation. It has two cloud-based components, Heimdal Dashboard and Heimdal Agent both compatible with Azure.
No passwords are involved, but the platform does rely on agents installed on endpoints. The passwordless approach to authentication is assisted by automation built into the admin dashboard. The Heimdal dashboard gives admins the ability to block requests that come from compromised endpoints or authorize for escalation at the endpoint. An auto-approval flow can be set up with rules defined and automatic de-escalation on threat. Admins can also define and apply a rule-based system and define individual rights within an AD group. The ability to revoke privileges escalation rights is based on DNS or AV detections of anomalous activity. This solution on dependent on Microsoft Azure, Active Directory and Azure Active Directory environments with identity management largely outsourced Active Directory settings.
Some interesting capabilities have been added to the mix. A "PAM Compliance" view available from a tab gives some insight into user behaviour such as elevations (a kind of micro PUBA) and the AD Groups the user belongs to. There is also automatic blocking of revoked Admins and an API linking PAM directly to ServiceNow to process privileged service requests. To protect against Ransomware and other attacks, a Zero Trust module can block malicious file execution and users not in whitelisted groups are automatically blocked. More capabilities are coming to extend this platform more for the enterprise including JIT access, password vaulting and session management. A new Access Control List grants users’ permissions to manage the Settings and Dashboard actions; this will be further refined and enhanced in the short/ midterm product strategy.
While this is specialist and limited PAM product, in the new era of remote and home working Heimdal may find willing customers, especially if it continues to add more PAM capabilities. All organizations, even those with existing PAM portfolios may benefit from a dedicated, easy to use cloud-based tool that simplifies controls and monitors Remote Privileged Access (RPA) requests for rapid elevated access.
This software really works best when integrated with Heimdal's other Application Control, Endpoint Protection and Vulnerability Management tools. Heimdal offers a bundle of its PAM tool with Application Control, to add application white/blacklisting on top of access management at the endpoint, which will have appeal to some buyers or department heads.

| Ratings | Security |  |
| Functionality |  |
|
| Deployment |  |
|
| Interoperability |  |
|
| Usability |  |
| Strengths |
|
| Challenges |
|
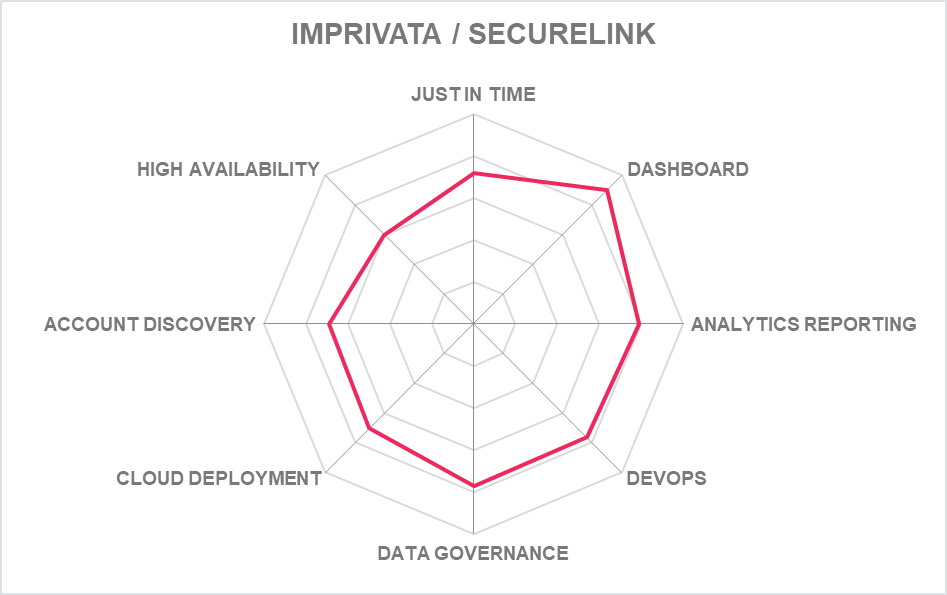
5.12 Imprivata – PAM
Imprivata is a US based identity management company that is widely known in the healthcare sector. It boosted its expertise in PAM through the acquisition of Xton in 2021. The Imprivata Privileged Access Management solution is agentless and supports RDP, SSH and HTTP(s) proxies and HTML 5 that can record sessions, keystrokes, and file transfers.
The solution benefits from weekly updates including feature requests and bug fixes – part of the company's philosophy that security software should be updated often, something hard to argue with if updates are pushed. Updates are deployed via the GUI and latest improvements include a Zero Trust login and session recording for AWS command line and automation tools, access to isolated networks without firewall changes and an improved Administrator Dashboard.
Imprivata PAM provides a web-based, password vault with accounts discovery, shared account password management and privileged session management capabilities, including password rotation, access request workflows and session and keystroke recording with playback. Credentials never leave the vault, and the solution also supports Just-in Time (JIT) provisioning.
While Imprivata does not provide full privilege elevation and delegation management (CPEDM) capabilities, it offers support for elevated script automation for routine privilege escalation tasks, enhancing administrator efficiency.
Imprivata PAM is a self-hosted solution that supports Windows, Linux Server installations (including RedHat) on-premises or for the cloud. There are two versions: Enterprise Password Vault which provides basic PAM functionality and the Imprivata Access Manager for Enterprise that adds workflows, password rotation, discovery remote access and full API integration among other features. MFA and SSO is supported through integration with AzureAD, Okta, One Sign, WatchGuard and Duo Security. For a relatively new platform, Imprivata offers a wide PAM technology portfolio that aligns well with the market direction and supports emerging PAM requirements of organizations. Imprivata offers integrations with well-known ITSM, SIEM and MFA providers, and is a scalable solution for on-premises, hybrid, and cloud deployments.
Based on open software and standards, Imprivata PAM offers an unlimited subscription pricing model and thereby presents a viable alternative to many established PAM vendors, particularly in the mid-market segment. An interesting alternative option, and one to watch – but needs more capabilities which will undoubtedly come as Imprivata beds its PAM platform in with its existing IAM portfolio – which in turn should benefit from the cloud native PAM tools on offer here.

| Ratings | Security |  |
| Functionality |  |
|
| Deployment |  |
|
| Interoperability |  |
|
| Usability |  |
| Strengths |
|
| Challenges |
|
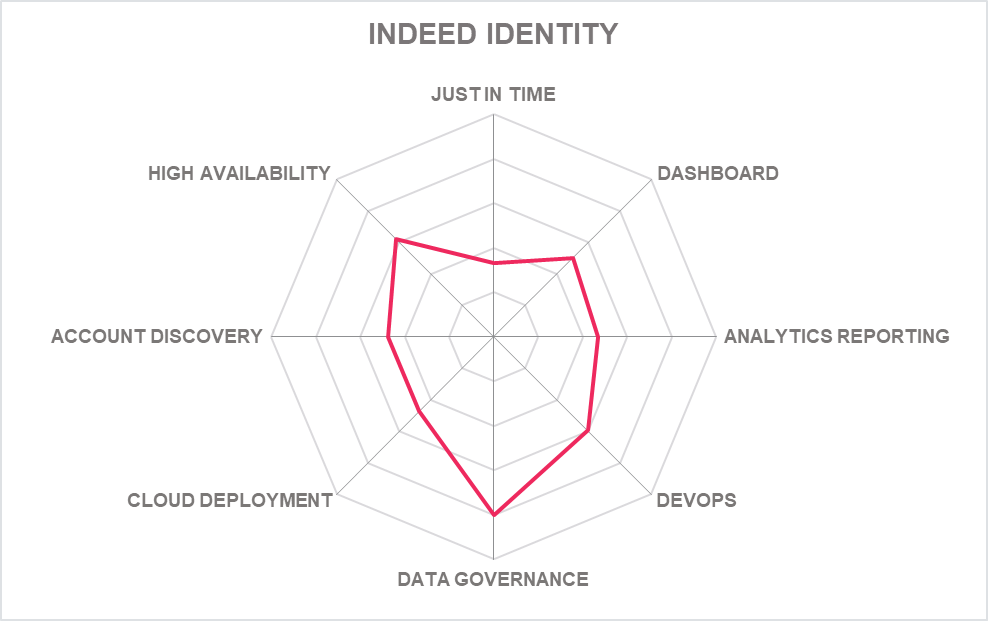
5.13 Indeed Identity – Indeed Privileged Access Manager
Indeed Identity is a Lithuanian IAM vendor founded in 2011. It has now branched out into PAM, reflecting a recent trend in the industry of IAM and PAM technologies coming closer together. Currently the platform runs as software on-premises only, with no cloud or SaaS options – although this is on the company's two-year roadmap.
Despite current deployment limitations, the platform is well featured for basic PAM capabilities, including vaulting, session recording, and shared account management. Also on the plus side is a thoroughly modern interface and UX, which older rivals in the market could learn from. There is Device Discovery - search in the AD/LDAP and import a list of target resources into PAM, and Account Discovery with ability to import privileged accounts into Indeed PAM.
Capabilities that stand out are an SSO module that connects to any client application plus 2FA supported out of the box without any third-party applications needed. The base code of Indeed Identity's PAM server is lean and designed for easy integration into legacy and new architecture. The company also designed the platform to be configured on privileged and security policies such as approved SSH commands and the policies and rules around session recording.
A good basic package that ticks many of the boxes but has some notable omissions that would be essential for many buyers. These include Cloud support, EPM, PUBA, Privilege Elevation, and JIT. But there is support for AAPM assisting with some DevOps which is good for those looking for that.
The solution does basic PAM stuff well and is very well designed but without its omissions and shortcoming being addressed soon, it is difficult to see Indeed Identity becoming truly competitive in the PAM space but there is promised development focus on Just-In-Time and access control improvements and usable integration via API – which Indeed Identity should take further.

| Ratings | Security |  |
| Functionality |  |
|
| Deployment |  |
|
| Interoperability |  |
|
| Usability |  |
| Strengths |
|
| Challenges |
|
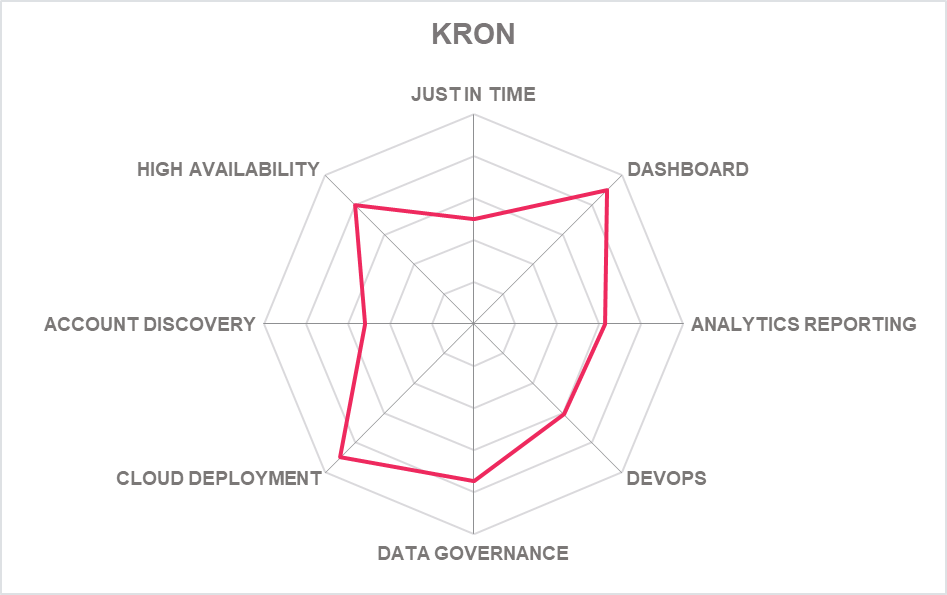
5.14 Kron – Krontech Single Connect
Based in Turkey, Krontech is an arm of Kron, a technology firm firm publicly listed on the Istanbul stock exchange. Krontech offers the Single Connect PAM suite which comprises eight modules to manage aspects of privileged access.
Krontech Single Connect features a "bottom-up" strategy for secrets onboarding. This translates as a visual hierarchical tree structure to manage secrets and more flexible policies for password generation (length, numbers, letters, special characters, alphanumeric characters). There is out of the box support for 60+ enterprise applications and systems.
The PUBA component has been enhanced with adaptive intelligence techniques, able to act according to risk scores and imminent security threats related to privileged accounts/access. Risk score calculations are made in 3 different dimensions: users, servers, sessions. Reports of all threat activity are also available for download. The interface and web GUI remain competitive along with the easy-to-use Desktop Client Application for Windows and MacOS, which sits alongside the WEB based interface.
Automation can be applied to recurring privileged tasks such as network port updates, DNS maintenance, router configuration, CMDB update automation (pre check, validation, and post check mechanism), as now supports integration with any ITSM system before running any task.
The Data Access Manager supports video recording and can enforce policy at the query level. The product can be accessed as a desktop client, web app or via a mobile app. While also supporting Putty, it features token based application to application password management. All sessions are recorded as MP4 files while there is good support for SIEM integration.
There is support for CPEDM, PUBA and PADLM which should be expected at this level of PAM solution. Supported third parties’ applications include Duo and Okta and management of access to cloud applications is supported on AWS, Azure and Google. Unusually, Single Connect has a built-in MFA manager called the Unified Access Manager which also includes support for SSO. Single Connects MFA Manager provides built-in MFA (multi-factor authentication) for Single Connect’s Session Manager and Direct Access Manager modules. In addition, MFA manager integrates with VPN servers, allowing MFA authentication at enterprise network access.
Single Connect’s Unified Access Manager provides built-in and pre-integrated TACACS+ and RADIUS servers that provide AAA (Authentication, Authorization and Accounting) services for network infrastructure and extends authentication, single-sign-on capabilities, and policy configurations of Active Directory to network infrastructure.
With easy-to-use SAPM and PSM capabilities, Krontech Single Connect may appeal to small and mid-size businesses (SMBs) with manual routine PAM tasks eliminated by useful privileged task automation, thereby accelerating leaner privileged operations. This remains a package worth further investigation and will benefit from improved DevOps capabilities, AAPM capabilities, a hosted SaaS version and further improvements to the UX.

| Ratings | Security |  |
| Functionality |  |
|
| Deployment |  |
|
| Interoperability |  |
|
| Usability |  |
| Strengths |
|
| Challenges |
|
| Leader in |  | 
|  | 
|
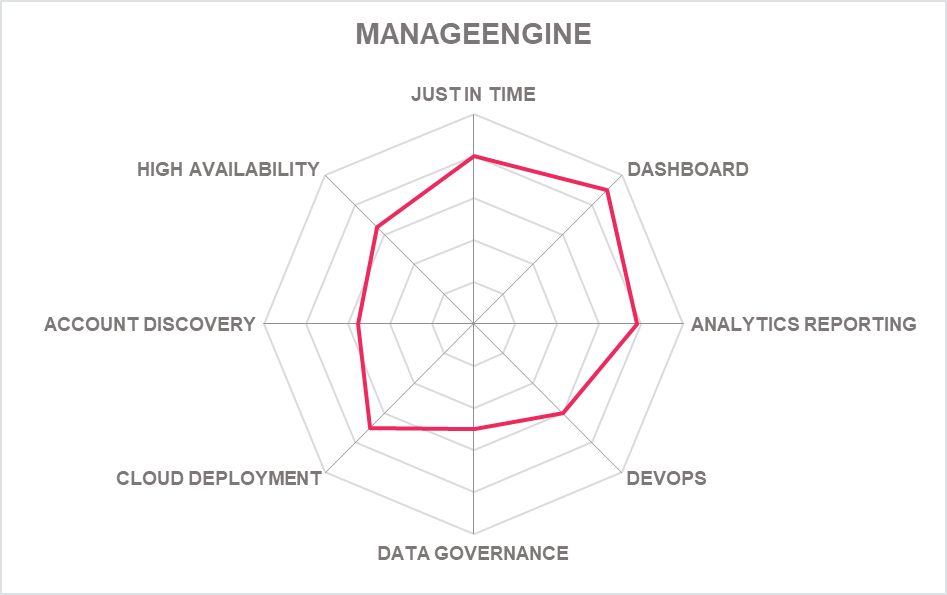
5.15 ManageEngine – PAM360
Headquartered in Pleasanton, US, ManageEngine is a part of the India-based Zoho Corporation founded in 1996. PAM360 is the company's main modular offering to the PAM market and offers key functionalities in an integrated fashion.
ManageEngine PAM360 encompasses PASM, Secrets management, encryption key management, certificate management, PEDM, AAPM and limited workflow automation. Password Manager Pro, Key Manager Plus and Access Manager Plus are point products in the portfolio, which cater to niche PAM use cases. They are also the key modules of PAM360 the enterprise PAM suite).
The platform promotes key management over more traditional password management, but still supports traditional password rotation with a proprietary vault technology. Privileged Account discovery works across Windows, Linux, Network devices and databases. Session management masks passwords from users when launching RDP, VNC, SSH and SQL sessions. All sessions can be recorded and PAM360 comprises tools for PAG, PUBA, SSL and SSH key management and workflow automation.
PAM 360 benefits from machine learning capabilities in its PUBA functions which assists with user behaviour patterning to detect anomalies. The interface for PUBA shares the same modern look as the rest of the solution and delivers a high level of risk scores including current high-risk servers, current high-risk users, and total number of anomalies. A highly useful resource for admins which offers drill down into more granular data on users.
ManageEngine makes a play of its "smart" workflow automation and there is credibility to this with integration with Automation Anywhere and integration with ITSM ticketing systems such as ServiceDesk Plus and Service Now. On a more fundamental PAM issue, PAM360 offers strong SIEM integration with Splunk, SumoLogic and Log360. DevOps is covered up to a point with integrations for Jenkins, Ansible, Chef and Puppet.
The self-service privilege elevation feature comes with built-in least privilege capabilities, where users will have minimal or no access to certain applications. Based on the merits of their requests, users will be provided with access to allow listed applications for a specific period, and the access to such applications will be revoked after the users have successfully carried out their actions. This includes managing and securing cloud infrastructure entitlements.
We would have liked to have seen more capability development rather than still waiting for native DevOps, cloud and PAMaaS but this remains one of the best platforms outside the Leadership space.

| Ratings | Security |  |
| Functionality |  |
|
| Deployment |  |
|
| Interoperability |  |
|
| Usability |  |
| Strengths |
|
| Challenges |
|
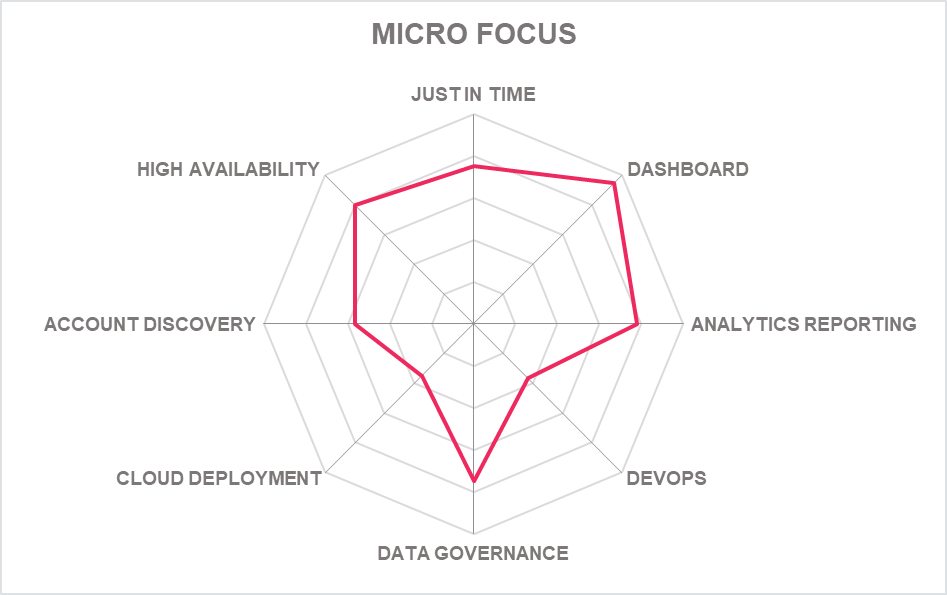
5.16 Micro Focus NetIQ Privileged Account Manager
Micro Focus, founded in 1976, has many solutions for organizations looking to transform operations and infrastructures. It markets its PAM platform under the NetIQ brand, a former acquisition, and now part of the company's CyberRes security portfolio.
In 2021 we said Looks like Micro Focus is getting back on track with its PAM play and there has been further incremental development of the platform. MFA is now an option for Privileged Access Elevation and SSO is available via IdP platforms, and improved search tools. Micro Focus is available on premises, in the cloud or as SaaS.
The integration of Net IQ Privileged Account Manager with Micro Focus Interset, its proprietary UEBA solution means that risk scores can be generated based on user behaviour anomalies, such as unusual applications accessed, time of day, geographical location, device used and other metrics. NetIQ Privileged Account Manager then uses this information in its decision-making process to provide a privileged session based on the user's risk score.
Elsewhere, new agentless capabilities for both Windows and Linux deployments should speed time-to-value requiring fewer components to be installed (and be vulnerable). The platform now provides real-time session streaming, for improved monitoring and control of privileged sessions. This allows a secondary user to audit a privileged session in real-time and make decisions based on detected risky behaviour and terminate the session if desired. Improvements have also been made to user interfaces across the platform and a new console allows quick toggling between multiple privileged sessions.
Administrators can configure privileged access permissions in a simpler, easier, and more meaningful way with Access Control, the latest policy engine. New agentless capabilities for Windows and Linux enable faster time-to-value by requiring fewer NetIQ PAM components and a better user experience for privileged users by providing a highly functional console that allows for quick switching between multiple privileged sessions.
The Access Control policy engine focuses on grouping resources based on similar access requirements within an organization and then granting access to users based on criteria such as privilege level, monitoring requirements, allowed access time, and so on. Access Control gives you quick access to information about Privilege Governance (who has what access).
The highest priority product capabilities planned on the product roadmap are securing privilege access in the cloud, which includes Cloud Consoles, SaaS applications, and Cloud Static and Dynamic Workloads. Additional product capabilities to be introduced include secure programmatic access to cloud, microservices, and SaaS applications to our privilege escalation functionality.
For its Application-to-Application management functionality, NetIQ PAM supports the creation and management of tokens for service accounts, IoT, bots, and other applications. There is now greater out-of-the-box support for DevOps tools such as Slack, Jenkins, Git, Splunk, Chef, Puppet, and Ansible and as part of a wider commitment to securing access in the cloud.
NetIQ PAM will evolve in Cloud by supporting dynamic and ephemeral accounts, enabling Security Token Services for Least Privilege Access, as part of the planned expansion of cloud and SaaS applications. Cloud dynamic resources are also enrolled as ephemeral machines to protect themselves in NetIQ PAM, with zero standing privilege accounts.
With these improvements and the solid PAM tools at its core discovery, vault, session management and recording, AAPM, EPM and SIEM Micro Focus NetIQ offers privileged session management across a variety of systems including enterprise business applications such as SAP, databases, and popular SaaS applications.

| Ratings | Security |  |
| Functionality |  |
|
| Deployment |  |
|
| Interoperability |  |
|
| Usability |  |
| Strengths |
|
| Challenges |
|
| Leader in |  | 
|  | 
|
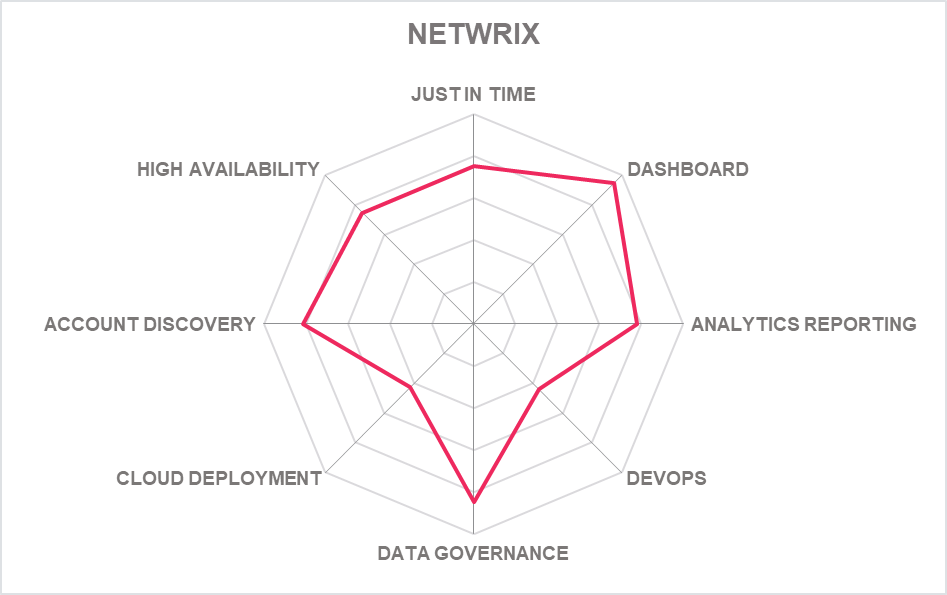
5.17 Netwrix – SbPAM
Netwrix was founded in 2006 and is headquartered in Irvine, California. Having acquired Stealthbits in 2021 it has now fully rebranded its PAM platform as Netwrix SbPAM.
Netwrix has made some technical enhancements of note: Security OpenID Connect and SAML 2.0 authentication, scheduled password rotation for all supported platforms and a browser extension for Chrome and Edge for improved web session recording. There is also a claimed 10-minute deployment option as ever such claims need verification in the real world, but the simplicity of SbPAM architecture suggests that rapid times could be achieved. We are also promised SSH key management and credential-based policies for AAPM soon.
There are four basic functions in the product: access control, session recording, editing and vaulting. This provides scheduled and on-demand credential rotation capability for all AD, Windows, Linux, Cisco and Azure AD). The design is to simplify PAM as much as possible by providing a fully JIT ephemeral approach to access and provisioning with as little as possible installed in the customer environment. Privileged accounts don't exist until someone is doing something, then they disappear. However, the product does also support the management and rotation of dedicated admin and other accounts as well as ephemeral accounts.
The key is BYOV or Bring Your Own Vault. Customers have the option to integrate a third-party vault via API from several leading PAM providers although 99% of customers choose Microsoft LAPS. Stealthbits built-in vault protects service accounts used for privilege escalation and can manage the passwords for existing privileged accounts used by administrators.
On the dashboard there is no long list of accounts, instead users select what they want to do and then the system provides access and provisions the account. When the session is finished the user is automatically logged out and all privileges are removed. It uses mesh architecture and provides scalability supporting Windows, Linux and Docker built on a .net core and can be run hybrid, on-premises, or in the cloud. Built-in task-based certifications are supported.
The Netwrix PAM suite offers hundreds of out-of-the-box auditing reports to fit a wide variety of common use cases. Both Netwrix PAM auditing products easily support custom scripting and reporting to aid in the configuration of novel auditing tasks. Netwrix PAM can manage privileged accounts, or use ephemeral accounts, when provisioning activity sessions on endpoints. Activities are fully customizable, so that any custom sequence of actions can occur during the pre-session, session, and post-session. Additionally, Netwrix PAM offers a password vault functionality. It also has a single pane of glass threat dashboard that surfaces a variety of threats across the environment in real-time and executes automated response playbooks.
Roadmap items include yet unspecified CIEM and ZTNA packages by end Q4, 2022 and tighter out of the box integration with common DevOps tools such as Ansible, Puppet and Chef. The next release of SbPAM will support custom roles for SbPAM console access. So, not only are SbPAM access policies and activities customizable, SbPAM console access will be customizable. This will allow for higher levels of fine-grained access for combinations of resources and users.

| Ratings | Security |  |
| Functionality |  |
|
| Deployment |  |
|
| Interoperability |  |
|
| Usability |  |
| Strengths |
|
| Challenges |
|
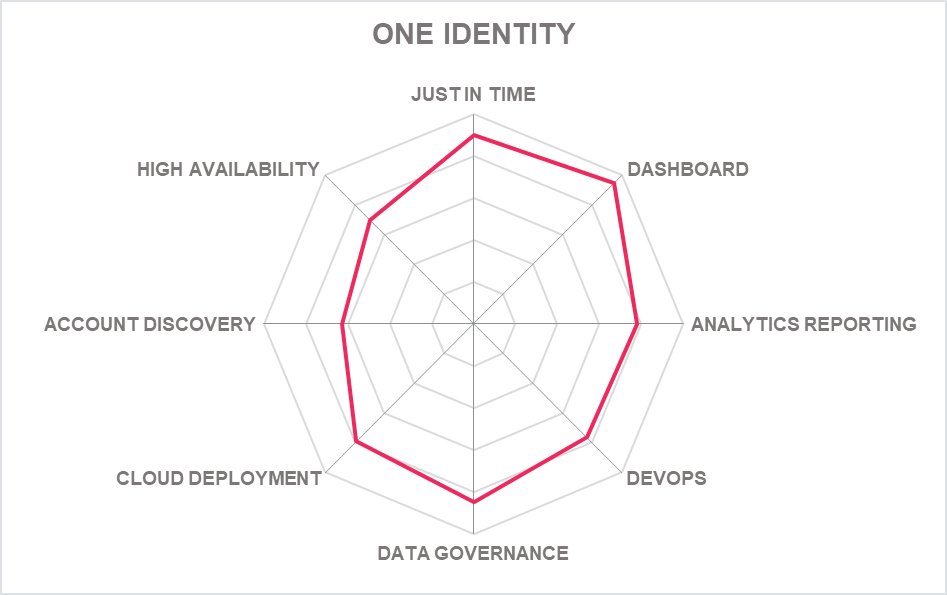
5.18 One Identity – Safeguard
California-based One Identity, a Quest Software business, specializes in IAM solutions and offers a range of products that fulfil the fundamentals of PAM. In addition, the company provides additional PAM capabilities for Unix/Linux AD bridging and privilege delegation. One Identity Safeguard is now a component of the One Identity Unified Identity Security Platform into which was recently added the OneLogin authentication suite.
The platform itself consists of Safeguard for Privileged Passwords, Safeguard for Privileged Sessions and Safeguard for Privileged Analytics. Safeguard for Privileged Passwords grants role-based access with automated workflows designed to speed up provisioning and authentication. Administrators can sign into the tool from a web browser with support for mobile devices while the tool is protected by two-factor authentication.
Safeguard for Privileged Sessions can record all privileged sessions and content is indexed to simplify searching for events and reporting. Safeguard for Privilege Analytics tracks user activity in real time and compares activity to session data collected from the wider IT environment. New additions include a SaaS solution, Safeguard on Demand and a Remote Privileged Access tool, Safeguard
A new secrets broker, based on HashiCorp and supporting the complete HashiCorp API, has been added to the package. This allows customers to manage secrets through the Safeguard vault or push secrets out to other secrets stores in the cloud (HashiCorp, Azure Key Vault, AWS Secrets Manager, etc.). This allows DevOps teams to use the secrets service that works best for them - a good move.
In a more specialized and welcome move, the Safeguard DevOps Service tool has been added which is a fully containerized service that brings a native level of connectivity from the Safeguard Vault to DevOps tools and environments. There is also Starling Connect for Passwords that allows customers to quickly subscribe to credential connectors for password rotation and discovery of cloud targets.
One Identity has improved its JIT provisioning for Safeguard which now allows privileges to be assigned at the exact time of credential check-out. Accounts in Active Directory that require privileges to perform a function can be added to the appropriate group(s) when the account is approved for check out, then removed.
All of One Identity's solutions offer an easy-to-use dashboard interface to control specific settings and task loads. The product can be implemented as a protocol proxy so that minimal changes are required to the network - and monitoring, recording, and analysis of privileged sessions is achievable without having to onboard any assets. Session activity can be captured via keystroke, mouse movement and windows viewed. All sessions are recorded as video and stored in a secure, searchable database.
One Identity also offers CPEDM and AD Bridge products as installable client packages. Safeguard for UNIX/Linux is a comprehensive suite delivering Unix-AD bridging, authentication, root delegation (SUDO enhancement) and centralized management of policies across Unix-based systems.
Privilege Manager for Windows offers CPEDM capabilities for Windows-based platforms. Finally, SIEM support is delivered with support for market leaders Splunk or Micro Focus ArcSight and MFA comes courtesy of One Identity Defender or via plug-ins for RSA, Yubikey, Okta, Duo and RADIUS. Safeguard now supports Sudo 1.9 which brings new security safeguards against user error and furthers JIT capability. With the addition of OneLogin this is now a competitive PAM option for many organizations.

| Ratings | Security |  |
| Functionality |  |
|
| Deployment |  |
|
| Interoperability |  |
|
| Usability |  |
| Strengths |
|
| Challenges |
|
| Leader in |  | 
|  | 
|
5.19 Remediant – SecureONE
Remediant was founded in 2013 and is based in San Francisco. Its SecureONE product has agent-less and vault-less technology at the core of the PAM platform that provides JIT access for all privileged accounts, abolishes shared accounts altogether, and stores no credentials at all.
SecureONE integrates with security platforms from Axonious (Cyber Asset Management), Carbon Black (EDR), CrowdStrike (EDR) SentinelONE (EDR) and, broader SIEM support. In terms of functionality the EDR integration permits session recording, associating relevant data with privileged access sessions. Basic IGA capability is also available with deeper IGA integration, specific to SailPoint.
OAM (Offline Access Management) now provides break-glass and scheduled on-demand rotation of local account credentials in case JIT access is not working due to the target system being offline. Remediant has also expanded its API endpoint integration count by 22% to further assist customer driven integrations.
It also supports role-based access control as well as attribute access control – however it lacks dedicated support for some more traditional advanced PAM capabilities such as AAPM. This is where pure JIT may fail for larger organizations that still need to vary privilege access safely. An agent less approach to endpoint access lowers risk of third-party breaches and speeds deployment times – which already promise to be quite rapid due to the small footprint of Remediant SecureONE. The company claims that 100,000+ endpoints can be managed within 2 hours.
While Remediant is focused on marketing an integrated JIT privilege access management solution, it also covers the basics well. It supports all major operating systems across desktops and servers and is available on cloud, on-premises or hybrid. For DevOps, it provides RESTfull API support and lightweight directory bridging for Linux systems. As for High Availability SecureONE supports HA, DR and HA+DR configurations. It can support HA configurations with up to 4 node fault tolerance. SecureONE also supports integration with several SIEM systems.
Remediant now offers two deployment options. The existing virtual appliance method that deploys 1-3 virtual appliances in the customer environment in a clustered configuration. This deployment mechanism offers HA and DR with flexible RTO and RPOs. For the SaaS offering, the customer can deploy several sensors (small virtual machines) in various environments. These sensors communicate directly with Remediant's SaaS console. Sensors can be added, removed or replaced without impacting service availability. A great step forward for SaaS based PAM.
However, the platform still lacks dedicated support for some more traditional advanced PAM capabilities such as AAPM but its cloud native posture and refusal to use passwords or agents is becoming more relevant.

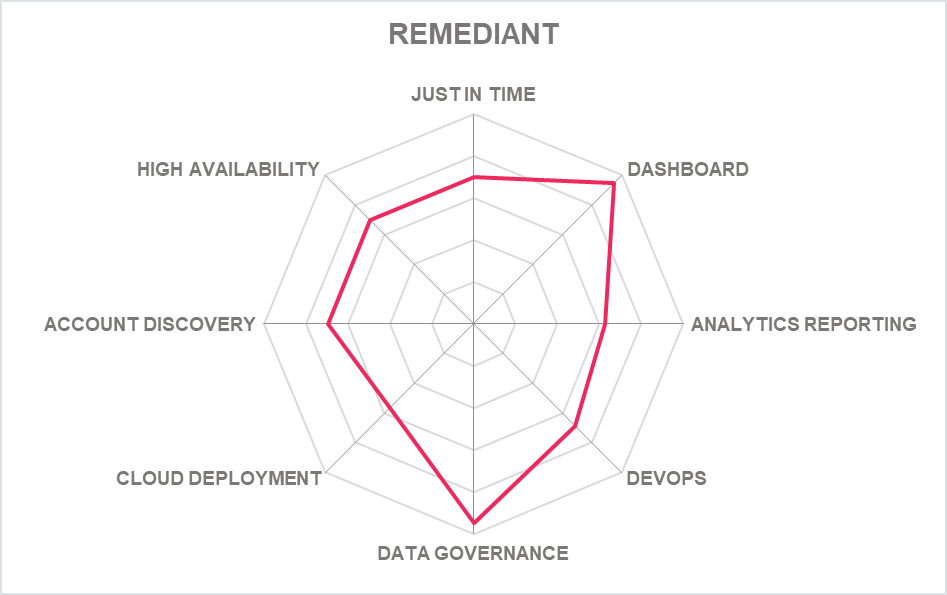
| Ratings | Security |  |
| Functionality |  |
|
| Deployment |  |
|
| Interoperability |  |
|
| Usability |  |
| Strengths |
|
| Challenges |
|
| Leader in |  | 
|  | 
|
5.20 Saviynt – Cloud Privileged Access Management
Saviynt is a US based company founded in 2010 that specializes in IGA and Identity solutions. It recently entered the PAM market with a SaaS cloud solution. Saviynt does provide a vault by default, but also allows customers to choose their own provide a vault allowing customers to choose their own. This allows customers to use existing including HashiCorp or Fortanix and other vault solutions with the Saviynt and the platform enables just-in-time access, role-based elevation, requests/approvals, ownership, succession management, workflows and governance
The solution is designed to run on all major cloud platforms, including Google, AWS and Azure. It is also fully compatible with Workday and Office 365 integrations, which is useful for organizations standardizing on SaaS based operations.
Saviynt Cloud PAM can automatically discover and secure privileged access to all the applications in the IT ecosystem — whether on-Prem or in the cloud and adopt a password-less experience for privileged accounts to reduce credential leak. Other capabilities include role-based access (good), session recording, log ingestion and just-in-time access to any application.
Saviynt's solution also comes with built-in Cloud Entitlements Manager (CIEM) features, which is good. In addition, as part of its converged Enterprise Identity Cloud (EIC) platform, Saviynt's cloud PAM comes with built-in IGA features. There is continuous discovery of cloud workloads and entitlements and monitoring of services and workloads for security errors or misconfigurations. A new Risk Exchange tool allows bi-directional data integration with 3rd party solutions such as SIEM and vulnerability management solutions. There is also Automated Backdoor Entry Protection, able to identify backdoor accounts and automatically disable, delete, based on policies - and alert and mitigate.
The web-based interface is designed to be user -centric and in this the company has succeeded in creating a very clean and simple interface. It is a bold move to create a PAM solution that runs only as a service. While it gives the developers control over iterative development, it also hands them greater responsibility for the integrity of privileged access management for their clients. Overall, this represents a promising addition to the ranks of PAM solutions, taking PAM as SaaS further and the company has exciting plans to add to the BYO concept. Development is under way to support BYO widgets and more out of the box dashboards in a future release. Saviynt is also looking at High Dynamic JIT for RPA – tools to automate many repetitive tasks. Interesting times at Saviynt.

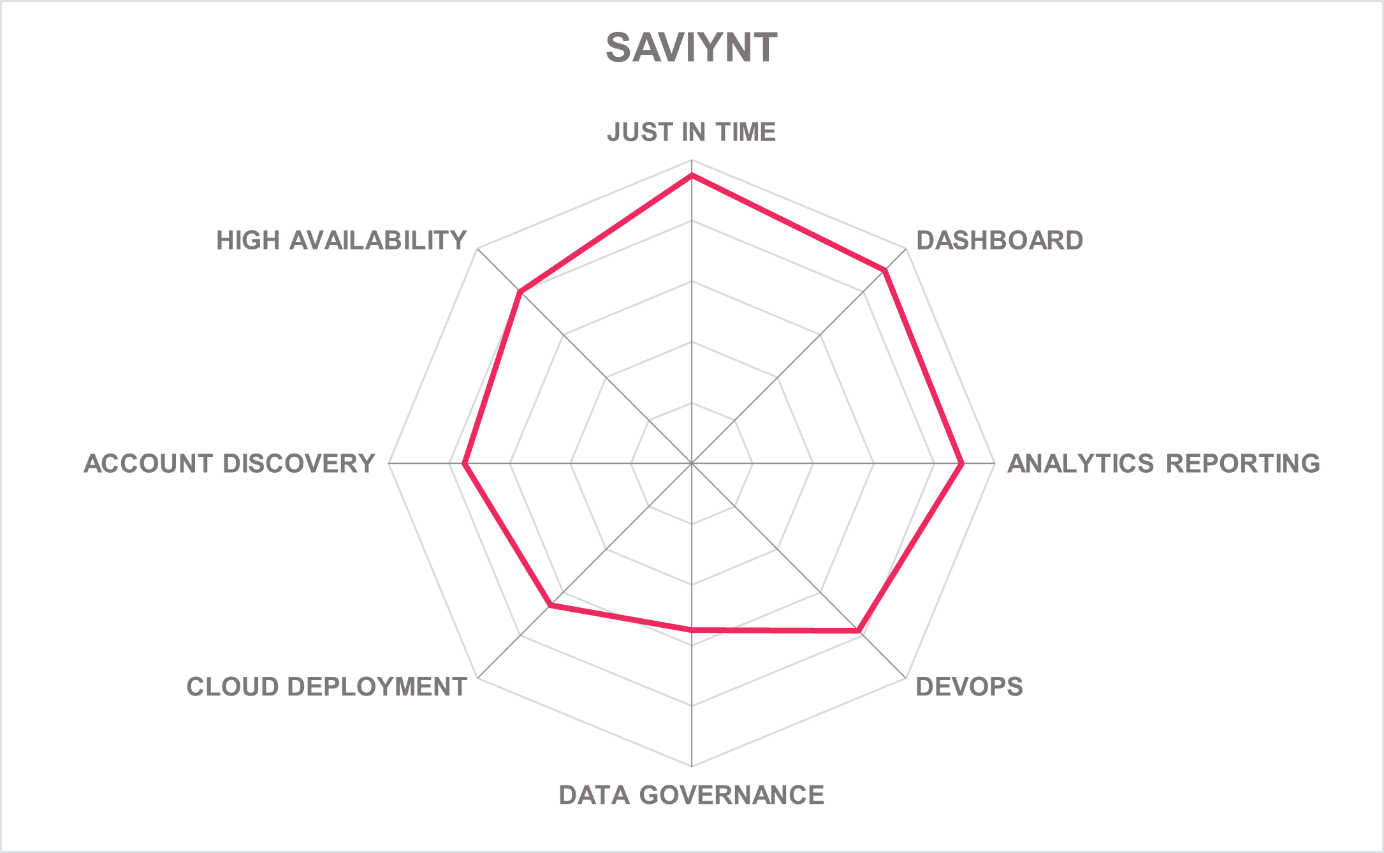
| Ratings | Security |  |
| Functionality |  |
|
| Deployment |  |
|
| Interoperability |  |
|
| Usability |  |
| Strengths |
|
| Challenges |
|
| Leader in |  | 
|  | 
|
5.21 Sectona – Security Platform
Founded in 2017, Mumbai (India) based Sectona offers four modules that cover basic PAM, Endpoint Privilege Management (EPM), Privileged Access Governance (PAG) plus DevOps Secrets Management.
Sectona offers JIT capability with Zero Standing Privilege (ZSP) now supported, Privileged Task Management (PTM) automates SSH and PowerShell commands to automate routine tasks while Privileged Account Lifecycle management is fully accessible from the Management Console.
Sectona's Common Session Management Framework can leverage sessions across browsers, local machines and jump servers. User access is governed by a unified policy framework & common connector element. There is support for cloud services from AWS, Azure and GCP. Sectona Security Platform is on the right side of cloud native with authentication available from any HTML5 supported browser or Sectona's native client, without the need of agents or plugins to be installed.
Sectona offers an in-built Plugin Designer Kit (PDK) that allows customers to develop their own connectors to facilitate PSM and SAPM for non-standard applications and does not require extensive coding experience thereby avoiding development costs. Sectona also offers an MSP edition of its software aimed at IT service providers wishing to offer managed PAMaaS, which is quite rare in the market, at present.
A highlight of the platform is Session Risk Scoring for threat analysis which gives an at-a-glance view of performance against pre-existing security and data theft categories. Risk alerts can be set for immediate notice of suspicious activities
It is up to speed with features such as Adaptive Authentication which will become more common on PAM in the future as well as Application to Application Password Management (AAPM) by using APIs and SSKs for many platforms. It is well positioned then to manage DevOps and containerization demands in the future. Sectona has added enhancements to Account Discovery, Cloud integrations and SCIM support, further strengthening a well-engineered platform that should scale well - to that end Sectona is planning to release a lightweight CIEM tool to compliment PAM in 2023.

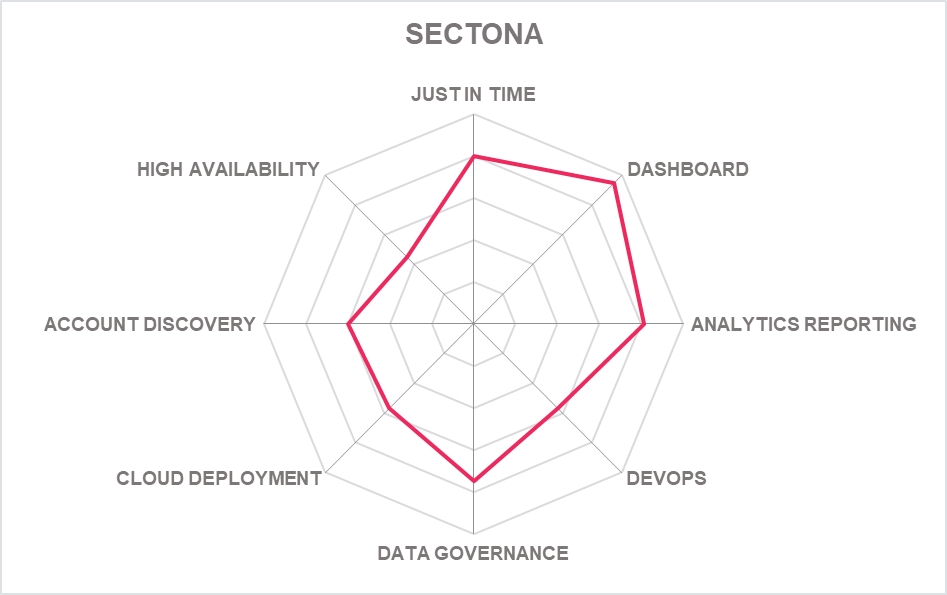
| Ratings | Security |  |
| Functionality |  |
|
| Deployment |  |
|
| Interoperability |  |
|
| Usability |  |
| Strengths |
|
| Challenges |
|
5.22 MT4 Tecnologia - Senhasegura
Based in São Paulo, Brazil, MT4 Tecnologia offers Senhasegura as its flagship PAM product. Senhasegura now has multiple modules available and presents comprehensive PAM capabilities. Senhasegura PAM is built over 15 tightly integrated functional components and is available as SaaS, on private and public cloud or in virtual or hardware appliance delivery formats.
Senhasegura PAM has a good mix of traditional and advanced capabilities and MT4 Tecnologia’s ambition to break into wider markets has resulted in solid development. The company has improved its use of biometrics – already used for MFA - with supporting algorithms designed to identify human keystroke patterns and alert to activity by unauthorized users on endpoints. Related to this is a module that collates user behaviour data to determine a risk score for all Privileged Users.
The User Security Posture Rating is used to calculate the probability of malicious actions given the history of the user's previous behaviour.
With each new privileged event executed by the user, the score is updated and dynamically influences password controls for the user.
Developers will appreciate the support in Task Manager Pro for Red Hat Ansible playbooks to create new privileged tasks. With Ansible it is easier
to create complex privileged routines and the tool integrates vendor modules already in its repository.
An agentless architecture allows for easy installation and configuration while preserving the full control of privileged settings. A set of built -in infrastructure modules offer high availability, load balancing and advanced monitoring capabilities. A new SaaS-based tool delivers Remote Privileged Access (RPA) that is agent-less and VPN-less, using the client cloud as the connection point to the network. The authentication is made via an MFA biometric validation on Senhasegura's Mobile App.
A new pack called "Senhasegura Cloud Entitlements" is designed to detect vulnerabilities on cloud-based accounts, adding a basic level of CIEM to the platform. With this analysis administrators can revoke standing and over privilege form users and identities.
MT4 Tecnologia now has a more powerful PAM proposition, with enhanced usability and forward thinking on the needs of developers and how PAM fits into Infrastructure as Code (IaC) environments. In addition to all basic PAM modules for account and password management, Senhasegura offers SSH key management, accounts discovery, AAPM, an endpoint MFA module plus much needed PUBA capability.
More developer focused tools are coming automation of scripts making integration with pipeline workflows much simpler through wizards, and a secret less option for the Senhasegura agent that will make it possible for applications to get authenticated without requesting passwords or secrets.

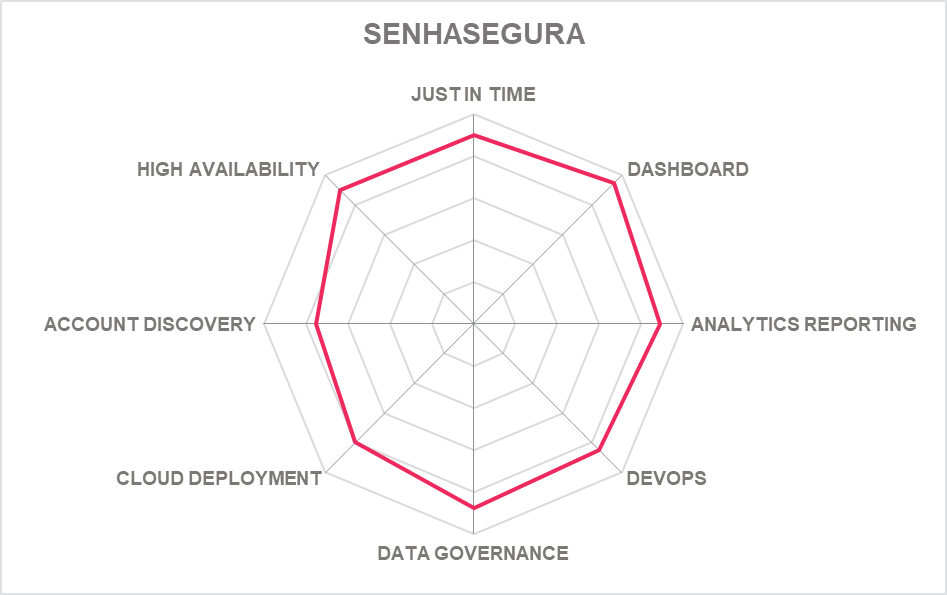
| Ratings | Security |  |
| Functionality |  |
|
| Deployment |  |
|
| Interoperability |  |
|
| Usability |  |
| Strengths |
|
| Challenges |
|
| Leader in |  | 
|  | 
|
5.23 SSH – PrivX
Based in Helsinki, Finland, SSH offers PrivX as its primary product for the PAM market. PrivX offers an alternative to traditional account & password management methodologies. It provides ephemeral (short-lived) certificate based Just-In-Time (JIT) access for SSH and RDP protocol authentication.
This approach can reduce the overhead management that typically comes with password vaulting solutions. PrivX does however come equipped with two vaults (user exposed & PrivX admin only access) providing the best of both worlds. In addition to the already existing key vault for admins, the new PrivX Secrets Vault allows for secrets to be stored and retrieved by users from the UI or automated processes.
Newly added functionality for X.509 certificate support further expands the range of targets accessible via certificate-based authentication, including Tectia SSH servers and devices from but not limited to vendors such as Cisco.
It is an innovative approach but one that brings functional and security advantages – access is faster, onboarding/offboarding of privileged users is quick and for most use cases there are no passwords to expose. Furthermore, credentials or secrets are masked from users when accessing targets using certificate-based authentication or vaulted passwords that are injected into target sessions.
Users can view a list of resources based on role memberships and select targets accordingly. User & Group information is automatically synchronized through seamless IGA/IDM integration capabilities. PrivX currently supports AD, Azure AD, LDAP/s, AWS Cognito, in addition directories from IAM systems using OIDC and SCIM claims are also supported.
While the core product is deliberately lean, it integrates with third parties to add functionality for SIEM, ticketing systems and HSM through APIs. In addition to the UI, Native Clients are supported for SSH and RDP with little to no loss in functionality over the main UI use. All SSH, RDP, HTTPs and VNC sessions are audited, logged and can be recorded for compliance, forensics or training purposes.
PrivX offers accountability of user activities even when shared target accounts are in use, since PrivX associates a user ID to every session. PrivX integrates with SIEM, UEBA/BAD systems. Other important areas of functionality covered include SAPM, AAPM, PADLM, PUBA and CPEDM but endpoint privilege management is missing here.
However, PrivX reduces the need for traditional endpoint security by isolating the user's local machine from the target. When connecting via its UI, target connections take place within a containerized (HTML5) browser session, meaning zero exposure to user local machines. This method of access also enables RPA (remote privilege access) without the need to manage external user/3rd party workstations which is ever more prevalent with today's distributed work practices.
PrivX has already secured the most important step in any CI/CD pipeline using ZT ephemeral certificates: access to code repositories such as Gitlab/Github. SSH plan to extend integrations to CI/CD tooling, like Jenkins.
SSH PrivX can be deployed on standalone IaaC or on-premises virtual machine, there is tooling for deploying PrivX as infrastructure as code and a Kubernetes deployment.
The product remains an attractive alternative for many organizations seeking to reduce password management and leverage cloud native capabilities.

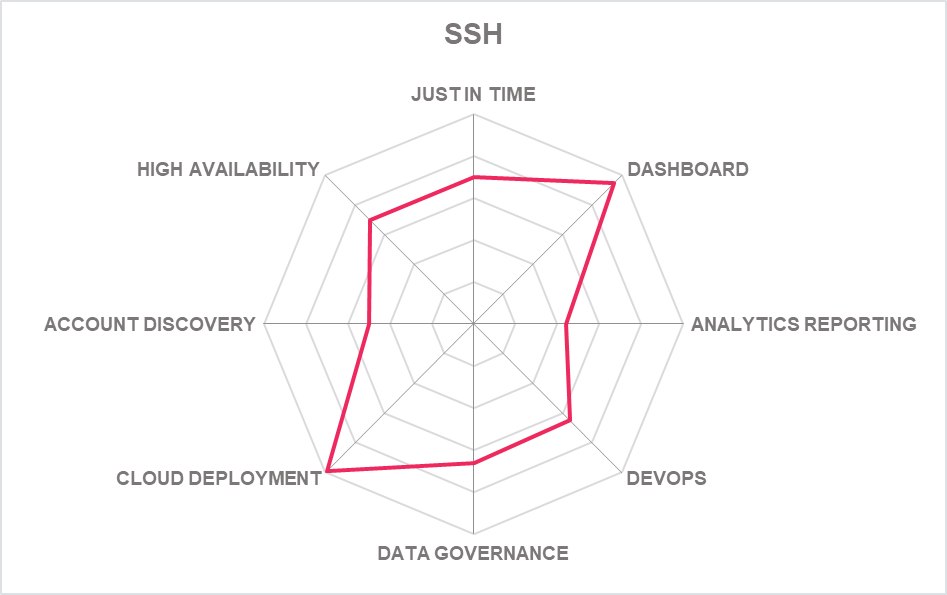
| Ratings | Security |  |
| Functionality |  |
|
| Deployment |  |
|
| Interoperability |  |
|
| Usability |  |
| Strengths |
|
| Challenges |
|
| Leader in |  | 
|  | 
|
5.24 Systancia – Cleanroom
Systancia is a software vendor specializing in secure remote access and workspace solutions based in France Systancia has several workplace and application virtualization tools. As part of this it offers the Cleanroom platform, which it developed as a PAM offering to the market. Systancia can now combine ZTNA and PAM within the same platform, as an extension to each other. It is available on-premises or as a service in four product lines: Systancia Cleanroom Session, Systancia Cleanroom Desk, Systancia Cleanroom Session Service and Systancia Cleanroom Desk Service.
Capabilities include Protocol-based session management and administration of resources (Web, SSH, RDP, VNC) (Cleanroom Session) and application-based session management and administration of resources (Cleanroom Desk). The platform also has an integrated vault, SSO and password rotation, account discovery and AAPM.
Systancia offers another new angle to privileged access management with a JIT approach based around virtualization. But instead of just providing ephemeral credentials it provides a totally virtualized environment for admins, separated from the real admin server and which can be disposed of after use. A vault and session manager are contained within the virtualized environment for sessions. The idea is that the core functional parts of PAM can be separated from log files, applications and unused secrets which remain on admin servers and only accessed for sessions as needed.
Since 2021, Systancia has made some solid capability and functional improvements to Cleanroom. Cleanroom Desktop Session with new support for FIDO 2 USB keys. There is also a much improved and fully graphical admin console with access to all logs, video logs, analysis of workflows and full export of logs top SIEM etc.
Systancia has opened the platform to customer development with an open-source API enabling automation of a limited number of functions, which undoubtedly will lead to more customization options suitable for more dynamic access applications. The company plans a migration of Systancia Cleanroom components to a microservices based architecture along with improved automation and orchestration for AWS deployments. Systancia has progressed in the cloud deployment of Systancia Cleanroom, with architecture and orchestration built for the AWS cloud infrastructure. We are also promised PEDM in the next iteration.
This is now a less specialist secure workplace delivery tool that offers some privileged capabilities and one that has been developed enough in the last year to provide an option for many more organizations. The integration with Systancia IAM and new focus on cloud native delivery, some DevOps stuff and privileged access options has made it much more interesting in this company.

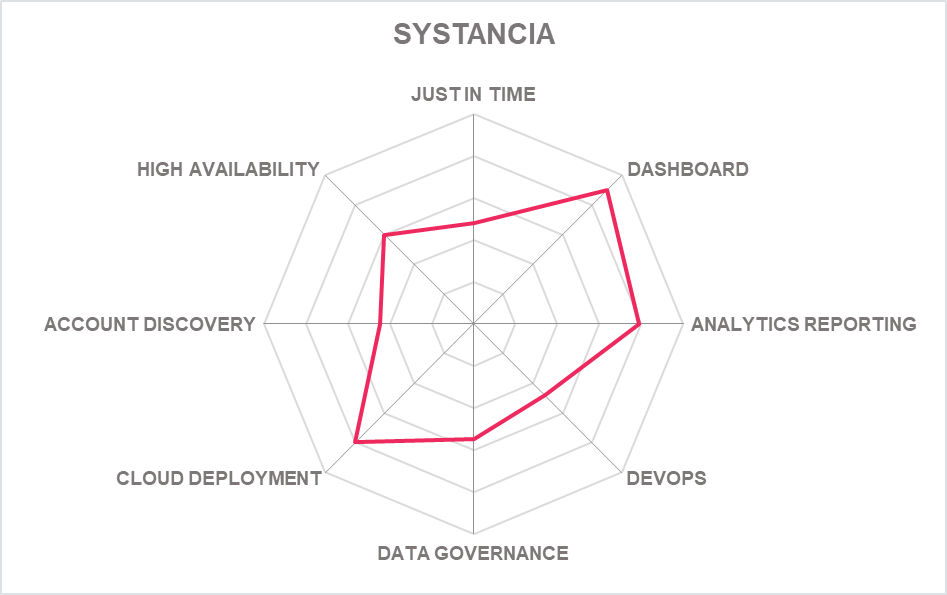
| Ratings | Security |  |
| Functionality |  |
|
| Deployment |  |
|
| Interoperability |  |
|
| Usability |  |
| Strengths |
|
| Challenges |
|
5.25 WALLIX – PAM4ALL
Based in France, WALLIX provides WALLIX PAM4ALL as its primary PAM product in the market. At the core is password management, session management and access management with built-in access request and approval capabilities.
WALLIX PAM4ALL consists of five major components that together form a solid foundation for enterprise level PAM: Session Manager, Password Manager (Vault), Access Manager, Privilege Elevation and Delegation Manager (PEDM) and Application to Application Password Manager (AAPM). To complete the picture, WALLIX PAM4ALL also supports WALLIX BestSafe to deliver an in-house compatible Endpoint Privilege Management (EPM) solution. Multi Factor Authentication (MFA) is also available.
WALLIX has made improvements to password management; AAPM has the capacity to provide virtual filesystem monitoring and replace on the fly placeholders with passwords for applications which rely on passwords being present in a configuration file. WALLIX PAM4ALL now has real time and extendable reporting and dashboarding capacities provided based on service options, based on the profile orientation for auditors and functional administrators. A new Access Manager provides access over native RDP clients. Only authorized applications can read this password automatically from the filesystem. New plugins have been released to allow Azure AD password rotation, and new database systems to be managed.
Sensibly, WALLIX has identified CIEM functionality scope as strategic initiative to explore in 2023, to expand deeper into identity security posture management controls like governance of entitlements, identity analytics as well as PAM and IGA process integrations. A new central console for PAM and EPM will facilitate the deployment, management, and elevation of least privilege rules. The PAM4ALL management console for PAM and EPM will allow central control of privileged permission to timed minimums, pushing the JIT approach further into the platform.
By building on its existing capabilities for password management and privileged session management (PSM) and adding enhanced EPM, AAPM and better DevOps support, WALLIX now has a highly competitive level of PAM capabilities that should be seriously considered by buyers in all organizations. The new product branding suggests a better marketing approach also, lending itself well to the new era of CIEM type capability adoption and much wider interpretation of what is privileged access in all organizations. WALLIX is now well established among the leaders and can only improve its capabilities. – we wish them bon chance!

| Ratings | Security |  |
| Functionality |  |
|
| Deployment |  |
|
| Interoperability |  |
|
| Usability |  |
| Strengths |
|
| Challenges |
|
| Leader in |  | 
|  | 
|
6 Vendors to Watch
6.1 Britive
Britive was founded in 2018 and based in California. It develops access and entitlement management solutions for IaaS platforms deployed in multi-cloud environments. It added CIEM capabilities and security governance tools to the platform in 2021. It’s raison d’etre is ephemeral JIT access for all types of identities to all resources - data, servers, CSP, SaaS applications - in DREAM environments. In scenarios when ephemeral access is not feasible, Britive has introduced a cloud vault for static secrets and keys, which can also be accessed JIT. Due to Britive platform acting as an abstraction layer, machine and non-machine identities never see or have standing access to the application, cloud, or server layer. Britive leverages an API-first approach to grant users’ access to the target cloud platform or application with the level of privileges authorized for the user.
Why worth watching: While this is undoubtedly a lean cloud first entitlement platform, it retains several classical PAM capabilities such as automated account discovery, rule-based privileged escalation, and onboarding of privileged accounts, which will be useful to many potential customers.
6.2 Deep Identity
Based in Singapore, Deep Identity is a regional provider of Identity Management software, offering Deep PIM as its primary PAM product which is essentially built as software plug-ins over Deep Identity Manager and comes with Privileged Access Server (PAS) acting as a gateway to establish and manage access to the target systems. While Deep IM extends account provisioning and access request approval workflows to privileged access, Deep PIM lacks several basic PAM features that include privileged accounts discovery, shared account password management (SAPM) and controlled privilege elevation and delegation management (CPEDM).
Though PIM gateway provides support for privileged RDP connections to Windows servers and offers session logging and recording with text-based search and review capabilities, it lacks support for management of privileged accounts and activities in cloud applications and platforms.
With some good local presence in Asia, particularly Southeast Asia (SEA), Deep PIM is a good addition to existing Deep Identity Manager deployments to onboard additional privileged session management features.
Why worth watching: It appeals to organizations with basic PSM needs along with the requirements of regional delivery and integration support.
6.3 HashiCorp
San Francisco (US) based HashiCorp is a provider of application development and delivery management software for data centers. Built on an open-source foundation, HashiCorp offers a secure password vault that integrates with its application development and delivery management modules to offer a tightly integrated DevOps platform.
The vault is offered in three variants for individuals, teams and enterprises depending on the complexity of development and deployment processes involved. While the basic password vaulting features such as encryption, secure storage, keys rotation, vault agent, access control policies and credential checkout workflows are included in all the three vault variants, MFA, governance and features necessary to support multi-data centers environments such as disaster recovery and replication are only available as part of team and enterprise versions.
While not a complete PAM platform, HashiCorp offers password vaulting and secure application to application password management capabilities to support enterprise DevOps initiatives.
Why worth watching: While several other PAM vendors are now offering similar capabilities to suit DevOps, HashiCorp offers a good start for organizations looking to onboard PAM within application development and deployment processes.
6.4 Iraje
India based Iraje offers Privileged Identity Management (PIM) as a complete PAM solution with a compelling feature set and the flexibility to customize according to business requirements. Offering an agentless approach to PAM, Iraje supports a wide range of target systems and is available in software as well as virtual and hardware appliance formats.
Iraje offers a native database client, schema extender and database monitoring module in conjunction with its PIM product targeted at securing privileged database operations. There are additional modules available for 2FA and SSO, but lacks endpoint privilege management and advanced AAPM capabilities such as application or process fingerprinting.
Why worth watching: Iraje's PIM is targeted at SMBs in Asia and should appeal to customers that require the flexibility to customize PAM for a deeper auditing and monitoring of database operations across a distributed IT environment.
6.5 NRI Secure Technologies
Japan based NRI Secure Technologies offers SecureCube Access Check primarily providing Privileged Session Management (PSM) capabilities. Operating in a gateway-based approach, SecureCube Access Check extends BeyondTrust Powerbroker Password Safe for password management. NTT Software Corporation builds its iDoperation PAM solution based on Access Check to offer session recording, monitoring and review capabilities. Supporting approval request workflows with role-based access control policies, Access Check offers a distinct approach aimed at access control of privileged users. Access Check lacks Application to Application Password Management (AAPM) capabilities, but supports command filtering and detailed session monitoring and alerting capabilities. SecureCube Access Check also provides access control and monitoring of file transfers and database sessions to Oracle RDBMS.
Why worth watching: With the majority of its customers in Japan, SecureCube Access Check makes a good fit for East Asian organizations looking for regional integration support and detailed privileged session auditing and monitoring capabilities.
6.6 ObserveIT
ObserveIT provides a comprehensive agent-based Session Management platform that is deployable and scalable across a variety of IT systems. ObserveIT is one of a few specialized vendors that originated in Session Recording and Monitoring (SRM) and extended it to include other PSM features. It offers detailed user behaviour analysis and live session response features.
In addition to monitoring and recording of both CLI and GUI type sessions in visual formats that allows creation of detailed user activity log of the recorded data, ObserveIT offers advanced user behaviour analytics that detects and alerts anomalous user behaviour. Observe IT also offers live session response that allows for the interruption of sessions at runtime based on information fed from user behaviour analytics or through external products such as SIEM (Security Information and Event Management) tools.
With visual endpoint recording, ObserveIT can capture sessions across a variety of systems, supporting all major protocols such as RDP (Remote Desktop Protocol) including the Citrix variants, SSH, Telnet and direct logins to application consoles.
Why worth watching: An agent-based approach allows for detailed logging and therefore a more meaningful and efficient activity search in contrast to other similar solutions that are primarily proxy or gateway-based.
6.7 Venafi
US based Venafi offers TrustAuthority, a machine identity protection platform that also offers extensive SSH key management for securing privileged access gained through SSH keys across organizations of all sizes and verticals. SSH keys are used for privileged operations in a Unix environment and pose significant threats to security as most organizations don't have a policy pertaining to management and rotation of SSH keys. Venafi TrustAuthority offers continuous discovery, inventory and monitoring of SSH keys across the IT infrastructure and enables automated key rotation.
Venafi TrustAuthority delivers centralized SSH key management and provides enterprise-wide visibility into SSH key inventories and SSH trust relationships. Venafi also offers automation of the SSH key lifecycle from key provisioning to decommissioning, thereby securing and controlling all SSH keys to minimize the risk of unauthorized access to critical systems.
Venafi isn't categorized as a pure-play PAM vendor by KuppingerCole as it doesn't provide basic common features required to be qualified as a PAM vendor. While several vendors offer SSH key management support as part of their SAPM, Venafi provides one of the most advanced SSH key management platforms in the market.
Why worth watching: Venafi appeals to organizations that have a critical security requirement to gain visibility and control over unmanaged SSH keys and other credentials used for privileged access.
7 Related Research
Leadership Compass Identity as a Service (IDaaS) IGA
Leadership Compass Privileged Access Management
Leadership Compass Identity Governance & Administration
Leadership Compass Access Management
Market Compass IGA Solutions for ServiceNow Infrastructures
Leadership Compass: Access Governance & Intelligence - 71145
Leadership Compass: Access Management and Federation - 71147
Leadership Compass: Adaptive Authentication - 71173
Leadership Compass: CIAM Platforms - 79059
Leadership Compass: Cloud-based MFA Solutions - 70967
Leadership Compass: Dynamic Authorization Management - 70966
Leadership Compass: Identity Provisioning - 71139
Leadership Compass: Identity as a Service: Single Sign-On to the Cloud (IDaaS SSO) - 71141
Leadership Brief Prepare and Protect against Software Vulnerabilities
Advisory Note Redefining Access Governance
8 Methodology
8.1 About KuppingerCole's Leadership Compass
KuppingerCole Leadership Compass is a tool which provides an overview of a particular IT market segment and identifies the leaders within that market segment. It is the compass which assists you in identifying the vendors and products/services in that market which you should consider for product decisions. It should be noted that it is inadequate to pick vendors based only on the information provided within this report.
Customers must always define their specific requirements and analyze in greater detail what they need. This report doesn’t provide any recommendations for picking a vendor for a specific customer scenario. This can be done only based on a more thorough and comprehensive analysis of customer requirements and a more detailed mapping of these requirements to product features, i.e. a complete assessment.
8.2 Types of Leadership
We look at four types of leaders:
- Product Leaders: Product Leaders identify the leading-edge products in the particular market. These products deliver most of the capabilities we expect from products in that market segment. They are mature.
- Market Leaders: Market Leaders are vendors which have a large, global customer base and a strong partner network to support their customers. A lack in global presence or breadth of partners can prevent a vendor from becoming a Market Leader.
- Innovation Leaders: Innovation Leaders are those vendors which are driving innovation in the market segment. They provide several of the most innovative and upcoming features we hope to see in the market segment.
- Overall Leaders: Overall Leaders are identified based on a combined rating, looking at the strength of products, the market presence, and the innovation of vendors. Overall Leaders might have slight weaknesses in some areas, but they become Overall Leaders by being above average in all areas.
For every area, we distinguish between three levels of products:
- Leaders: This identifies the Leaders as defined above. Leaders are products which are exceptionally strong in certain areas.
- Challengers: This level identifies products which are not yet Leaders but have specific strengths which might make them Leaders. Typically, these products are also mature and might be leading-edge when looking at specific use cases and customer requirements.
- Followers: This group contains vendors whose products lag in some areas, such as having a limited feature set or only a regional presence. The best of these products might have specific strengths, making them a good or even best choice for specific use cases and customer requirements but are of limited value in other situations.
Our rating is based on a broad range of input and long experience in that market segment. Input consists of experience from KuppingerCole advisory projects, feedback from customers using the products, product documentation, and a questionnaire sent out before creating the KuppingerCole Leadership Compass, and other sources.
8.3 Product Rating
KuppingerCole Analysts AG as an analyst company regularly evaluates products/services and vendors. The results are, among other types of publications and services, published in the KuppingerCole Leadership Compass Reports, KuppingerCole Executive Views, KuppingerCole Product Reports, and KuppingerCole Vendor Reports. KuppingerCole uses a standardized rating to provide a quick overview on our perception of the products or vendors. Providing a quick overview of the KuppingerCole rating of products requires an approach combining clarity, accuracy, and completeness of information at a glance.
KuppingerCole uses the following categories to rate products:
- Security
- Functionality
- Deployment
- Interoperability
- Usability
Security is a measure of the degree of security within the product / service. This is a key requirement and evidence of a well-defined approach to internal security as well as capabilities to enable its secure use by the customer are key factors we look for. The rating includes our assessment of security vulnerabilities and the way the vendor deals with them.
Functionality is a measure of three factors: what the vendor promises to deliver, the state of the art and what KuppingerCole expects vendors to deliver to meet customer requirements. To score well there must be evidence that the product / service delivers on all of these.
Deployment is measured by how easy or difficult it is to deploy and operate the product or service. This considers the degree in which the vendor has integrated the relevant individual technologies or products. It also looks at what is needed to deploy, operate, manage, and discontinue the product / service.
Interoperability refers to the ability of the product / service to work with other vendors’ products, standards, or technologies. It considers the extent to which the product / service supports industry standards as well as widely deployed technologies. We also expect the product to support programmatic access through a well-documented and secure set of APIs.
Usability is a measure of how easy the product / service is to use and to administer. We look for user interfaces that are logically and intuitive as well as a high degree of consistency across user interfaces across the different products / services from the vendor.
We focus on security, functionality, ease of delivery, interoperability, and usability for the following key reasons:
- Increased People Participation: Human participation in systems at any level is the highest area of cost and the highest potential for failure of IT projects.
- Lack of excellence in Security, Functionality, Ease of Delivery, Interoperability, and Usability results in the need for increased human participation in the deployment and maintenance of IT services.
- Increased need for manual intervention and lack of Security, Functionality, Ease of Delivery, Interoperability, and Usability not only significantly increase costs, but inevitably lead to mistakes that can create opportunities for attack to succeed and services to fail.
KuppingerCole’s evaluation of products / services from a given vendor considers the degree of product Security, Functionality, Ease of Delivery, Interoperability, and Usability which to be of the highest importance. This is because lack of excellence in any of these areas can result in weak, costly and ineffective IT infrastructure.
8.4 Vendor Rating
We also rate vendors on the following characteristics
- Innovativeness
- Market position
- Financial strength
- Ecosystem
Innovativeness is measured as the capability to add technical capabilities in a direction which aligns with the KuppingerCole understanding of the market segment(s). Innovation has no value by itself but needs to provide clear benefits to the customer. However, being innovative is an important factor for trust in vendors, because innovative vendors are more likely to remain leading-edge. Vendors must support technical standardization initiatives. Driving innovation without standardization frequently leads to lock-in scenarios. Thus, active participation in standardization initiatives adds to the positive rating of innovativeness.
Market position measures the position the vendor has in the market or the relevant market segments. This is an average rating over all markets in which a vendor is active. Therefore, being weak in one segment doesn’t lead to a very low overall rating. This factor considers the vendor’s presence in major markets.
Financial strength even while KuppingerCole doesn’t consider size to be a value by itself, financial strength is an important factor for customers when making decisions. In general, publicly available financial information is an important factor therein. Companies which are venture-financed are in general more likely to either fold or become an acquisition target, which present risks to customers considering implementing their products.
Ecosystem is a measure of the support network vendors have in terms of resellers, system integrators, and knowledgeable consultants. It focuses mainly on the partner base of a vendor and the approach the vendor takes to act as a “good citizen” in heterogeneous IT environments.
Again, please note that in KuppingerCole Leadership Compass documents, most of these ratings apply to the specific product and market segment covered in the analysis, not to the overall rating of the vendor.
8.5 Rating Scale for Products and Vendors
For vendors and product feature areas, we use a separate rating with five different levels, beyond the Leadership rating in the various categories. These levels are
- Strong positive: Outstanding support for the subject area, e.g. product functionality, or outstanding position of the company for financial stability.
- Positive: Strong support for a feature area or strong position of the company, but with some minor gaps or shortcomings. Using Security as an example, this can indicate some gaps in fine-grained access controls of administrative entitlements. For market reach, it can indicate the global reach of a partner network, but a rather small number of partners.
- Neutral: Acceptable support for feature areas or acceptable position of the company, but with several requirements we set for these areas not being met. Using functionality as an example, this can indicate that some of the major feature areas we are looking for aren’t met, while others are well served. For Market Position, it could indicate a regional-only presence.
- Weak: Below-average capabilities in the product ratings or significant challenges in the company ratings, such as very small partner ecosystem.
- Critical: Major weaknesses in various areas. This rating most commonly applies to company ratings for market position or financial strength, indicating that vendors are very small and have a very low number of customers.
8.6 Inclusion and Exclusion of Vendors
KuppingerCole tries to include all vendors within a specific market segment in their Leadership Compass documents. The scope of the document is global coverage, including vendors which are only active in regional markets such as Germany, Russia, or the US.
However, there might be vendors which don’t appear in a Leadership Compass document due to various reasons:
- Limited market visibility: There might be vendors and products which are not on our radar yet, despite our continuous market research and work with advisory customers. This usually is a clear indicator of a lack in Market Leadership.
- Declined to participate: Vendors might decide to not participate in our evaluation and refuse to become part of the Leadership Compass document. KuppingerCole tends to include their products anyway if sufficient information for evaluation is available, thus providing a comprehensive overview of leaders in the market segment.
- Lack of information supply: Products of vendors which don’t provide the information we have requested for the Leadership Compass document will not appear in the document unless we have access to sufficient information from other sources.
- Borderline classification: Some products might have only small overlap with the market segment we are analyzing. In these cases, we might decide not to include the product in that KuppingerCole Leadership Compass.
The target is providing a comprehensive view of the products in a market segment. KuppingerCole will provide regular updates on their Leadership Compass documents.
We provide a quick overview about vendors not covered and their offerings in chapter Vendors and Market Segments to watch. In that chapter, we also look at some other interesting offerings around the market and in related market segments.
9 Copyright
© 2023 KuppingerCole Analysts AG all rights reserved. Reproduction and distribution of this publication in any form is forbidden unless prior written permission. All conclusions, recommendations and predictions in this document represent KuppingerCole's initial view. Through gathering more information and performing deep analysis, positions presented in this document will be subject to refinements or even major changes. KuppingerCole disclaim all warranties as to the completeness, accuracy and/or adequacy of this information. Even if KuppingerCole research documents may discuss legal issues related to information security and technology, KuppingerCole do not provide any legal services or advice and its publications shall not be used as such. KuppingerCole shall have no liability for errors or inadequacies in the information contained in this document. Any opinion expressed may be subject to change without notice. All product and company names are trademarks ™ or registered trademarks ® of their respective holders. Use of them does not imply any affiliation with or endorsement by them.
KuppingerCole Analysts support IT professionals with outstanding expertise in defining IT strategies and in relevant decision-making processes. As a leading analyst company, KuppingerCole provides first-hand vendor-neutral information. Our services allow you to feel comfortable and secure in taking decisions essential to your business.
KuppingerCole Analysts AG, founded in 2004, is a global, independent analyst organization headquartered in Europe. We specialize in providing vendor-neutral advice, expertise, thought leadership, and practical relevance in Cybersecurity, Digital Identity & IAM (Identity and Access Management), Cloud Risk and Security, and Artificial Intelligence, as well as for all technologies fostering Digital Transformation. We support companies, corporate users, integrators and software manufacturers in meeting both tactical and strategic challenges and make better decisions for the success of their business. Maintaining a balance between immediate implementation and long-term viability is at the heart of our philosophy.
For further information, please contact clients@kuppingercole.com.